An Information Security Analyst primarily focuses on protecting an organization's data by implementing security measures and monitoring for breaches, ensuring compliance with regulatory standards. A Cybersecurity Analyst, while overlapping in responsibilities, often emphasizes identifying and mitigating cyber threats, conducting penetration tests, and analyzing cyber attack patterns. Both roles play critical parts in safeguarding digital assets but differ in scope, with Cybersecurity Analysts leaning more towards offensive and defensive threat management.
Table of Comparison
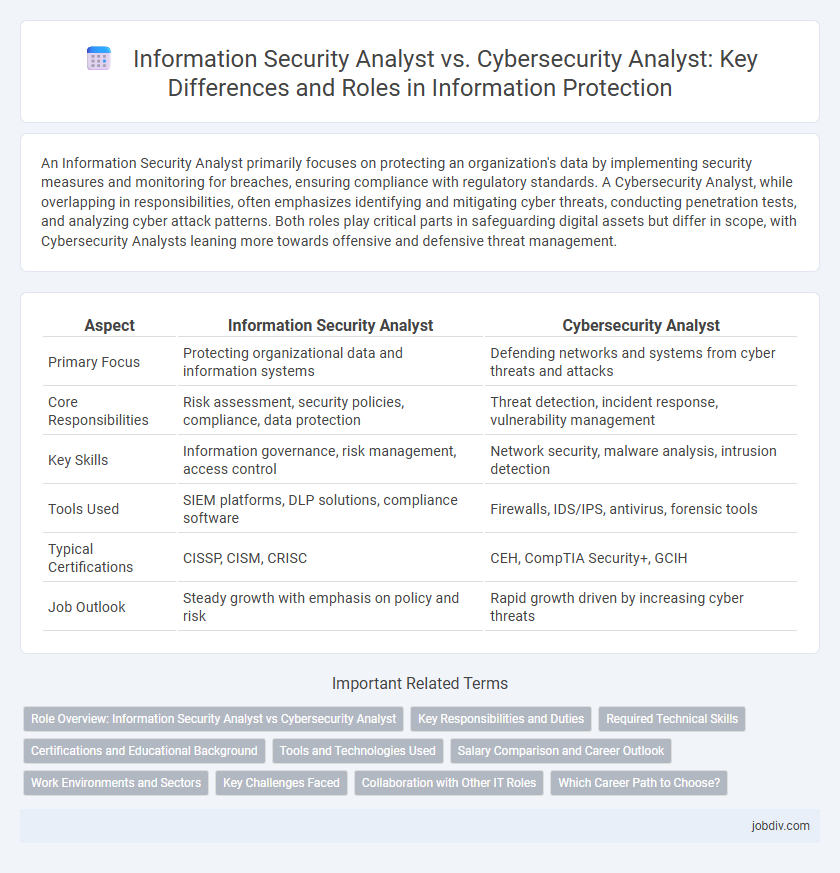
| Aspect | Information Security Analyst | Cybersecurity Analyst |
|---|---|---|
| Primary Focus | Protecting organizational data and information systems | Defending networks and systems from cyber threats and attacks |
| Core Responsibilities | Risk assessment, security policies, compliance, data protection | Threat detection, incident response, vulnerability management |
| Key Skills | Information governance, risk management, access control | Network security, malware analysis, intrusion detection |
| Tools Used | SIEM platforms, DLP solutions, compliance software | Firewalls, IDS/IPS, antivirus, forensic tools |
| Typical Certifications | CISSP, CISM, CRISC | CEH, CompTIA Security+, GCIH |
| Job Outlook | Steady growth with emphasis on policy and risk | Rapid growth driven by increasing cyber threats |
Role Overview: Information Security Analyst vs Cybersecurity Analyst
Information Security Analysts focus on protecting an organization's data and infrastructure by implementing security measures and monitoring for breaches. Cybersecurity Analysts specialize in identifying and mitigating cyber threats, often analyzing network traffic and responding to security incidents in real time. Both roles require expertise in risk assessment, security protocols, and incident response, but Cybersecurity Analysts typically have a more proactive role in threat detection and remediation.
Key Responsibilities and Duties
Information Security Analysts primarily focus on protecting an organization's data by implementing security measures such as firewalls, encryption, and intrusion detection systems. Cybersecurity Analysts concentrate on identifying threats, monitoring network traffic for suspicious activity, and responding to cyber incidents to prevent breaches. Both roles require expertise in risk assessment, vulnerability management, and compliance with security standards, but Cybersecurity Analysts often engage more directly in active threat mitigation and incident response.
Required Technical Skills
Information Security Analysts require proficiency in risk assessment, intrusion detection systems (IDS), and vulnerability management tools to protect organizational data. Cybersecurity Analysts must excel in malware analysis, penetration testing, and incident response to mitigate advanced cyber threats. Both roles demand expertise in firewall management, encryption protocols, and security information and event management (SIEM) systems for comprehensive defense strategies.
Certifications and Educational Background
Information Security Analysts often hold certifications such as CISSP, CISA, and CompTIA Security+, emphasizing risk management and compliance expertise, while Cybersecurity Analysts favor certifications like CEH, CompTIA Cybersecurity Analyst (CySA+), and GIAC Security Essentials (GSEC), focusing on threat detection and incident response. Educational backgrounds for Information Security Analysts typically include degrees in information technology, computer science, or information systems, whereas Cybersecurity Analysts often pursue specialized cybersecurity degrees or training programs. Both roles benefit from continuous professional development due to the evolving nature of cyber threats and technology.
Tools and Technologies Used
Information Security Analysts primarily utilize tools like SIEM (Security Information and Event Management) systems, vulnerability assessment software, and encryption technologies to safeguard organizational data. Cybersecurity Analysts deploy advanced intrusion detection systems (IDS), firewalls, endpoint protection platforms, and threat intelligence tools to identify and mitigate cyber threats. Both roles rely heavily on network monitoring solutions and incident response platforms to ensure comprehensive security posture management.
Salary Comparison and Career Outlook
Information Security Analysts earn a median annual salary of approximately $103,590, while Cybersecurity Analysts typically receive a slightly higher median salary near $107,000, reflecting the specialized skill set required. The career outlook for both roles is robust, with the U.S. Bureau of Labor Statistics projecting a 33% growth rate for Information Security Analysts from 2020 to 2030, driven by increasing cyber threats. Cybersecurity Analysts benefit from strong demand in sectors such as finance, healthcare, and government, offering expanded opportunities and potential salary advancement.
Work Environments and Sectors
Information Security Analysts typically work in corporate IT departments, government agencies, and financial institutions where protecting data and systems is critical. Cybersecurity Analysts often operate within specialized security firms, healthcare organizations, and defense sectors, focusing on threat detection and incident response. Both roles demand rigorous attention to security protocols but differ in environment intensity and sector-specific regulatory compliance.
Key Challenges Faced
Information Security Analysts often confront challenges related to protecting sensitive data from insider threats and ensuring compliance with evolving regulatory standards. Cybersecurity Analysts face persistent threats from sophisticated cyberattacks such as ransomware, phishing, and zero-day vulnerabilities that require continuous threat intelligence and rapid incident response. Both roles demand constant adaptation to advanced hacking techniques and emerging technologies to maintain organizational security posture effectively.
Collaboration with Other IT Roles
Information Security Analysts and Cybersecurity Analysts collaborate closely with IT teams such as network administrators, system engineers, and risk managers to implement robust security measures. They share threat intelligence and coordinate incident response efforts to mitigate vulnerabilities across the digital infrastructure. This interdisciplinary cooperation enhances proactive defense strategies and ensures comprehensive protection of sensitive data within the organization.
Which Career Path to Choose?
Information Security Analysts specialize in protecting organizational data by implementing security measures and monitoring for breaches, focusing on risk management and compliance frameworks. Cybersecurity Analysts primarily concentrate on identifying, analyzing, and responding to cyber threats through advanced threat detection tools and incident response strategies. Choosing the right career path depends on whether you prefer a broader scope of information protection or a more technical, hands-on role in combating cyber attacks.
Information Security Analyst vs Cybersecurity Analyst Infographic
 jobdiv.com
jobdiv.com