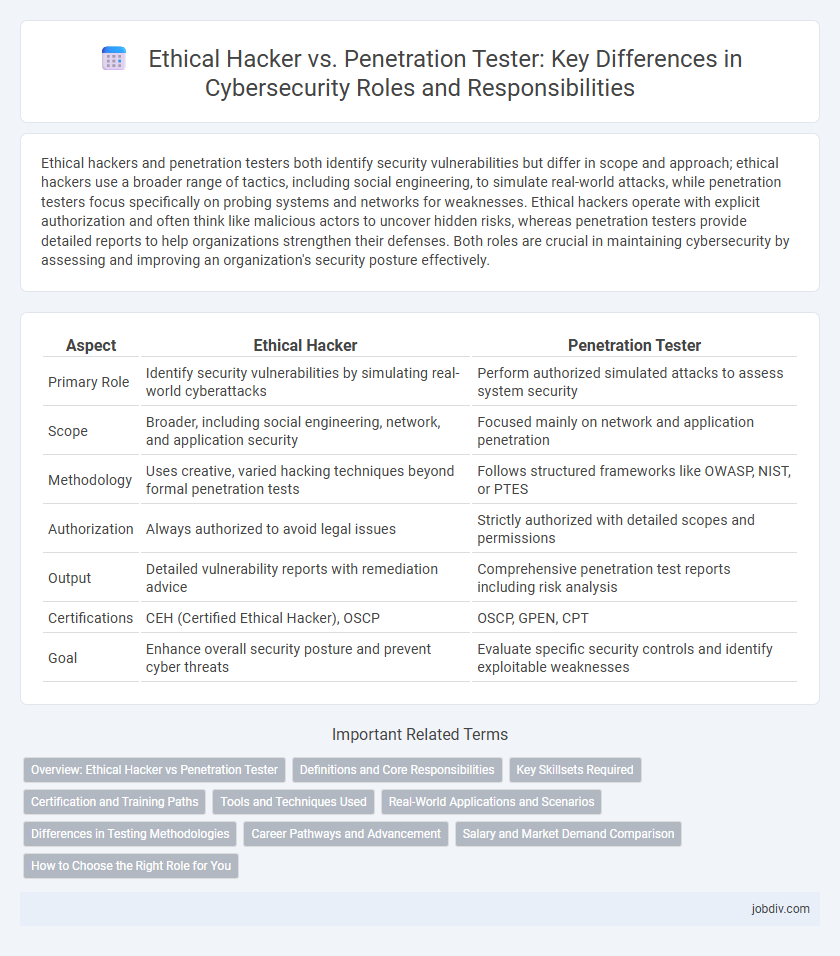
Ethical hackers and penetration testers both identify security vulnerabilities but differ in scope and approach; ethical hackers use a broader range of tactics, including social engineering, to simulate real-world attacks, while penetration testers focus specifically on probing systems and networks for weaknesses. Ethical hackers operate with explicit authorization and often think like malicious actors to uncover hidden risks, whereas penetration testers provide detailed reports to help organizations strengthen their defenses. Both roles are crucial in maintaining cybersecurity by assessing and improving an organization's security posture effectively.
Table of Comparison
| Aspect | Ethical Hacker | Penetration Tester |
|---|---|---|
| Primary Role | Identify security vulnerabilities by simulating real-world cyberattacks | Perform authorized simulated attacks to assess system security |
| Scope | Broader, including social engineering, network, and application security | Focused mainly on network and application penetration |
| Methodology | Uses creative, varied hacking techniques beyond formal penetration tests | Follows structured frameworks like OWASP, NIST, or PTES |
| Authorization | Always authorized to avoid legal issues | Strictly authorized with detailed scopes and permissions |
| Output | Detailed vulnerability reports with remediation advice | Comprehensive penetration test reports including risk analysis |
| Certifications | CEH (Certified Ethical Hacker), OSCP | OSCP, GPEN, CPT |
| Goal | Enhance overall security posture and prevent cyber threats | Evaluate specific security controls and identify exploitable weaknesses |
Overview: Ethical Hacker vs Penetration Tester
Ethical hackers simulate cyberattacks to identify security vulnerabilities in systems, using the same tools and techniques as malicious hackers but with authorization. Penetration testers conduct structured and systematic assessments to evaluate the effectiveness of an organization's security controls by exploiting weaknesses under controlled conditions. Both roles aim to enhance cybersecurity defenses, but ethical hackers often adopt a broader and more creative approach while penetration testers focus on detailed, methodical vulnerability analysis.
Definitions and Core Responsibilities
An ethical hacker systematically probes computer systems and networks to identify security vulnerabilities before malicious hackers exploit them, using techniques that simulate cyberattacks while adhering to legal and organizational guidelines. A penetration tester specializes in executing authorized simulated attacks on specific systems, applications, or networks to assess security weaknesses and provide detailed reports for remediation. Both roles aim to strengthen cybersecurity defenses, but ethical hackers take a broader approach to uncovering threats, whereas penetration testers focus on targeted, tactical assessments.
Key Skillsets Required
Ethical hackers require strong expertise in network protocols, vulnerability assessment, and social engineering tactics to identify and exploit security weaknesses effectively. Penetration testers must possess advanced skills in scripting languages, exploit development, and risk analysis to simulate cyberattacks comprehensively and evaluate system resilience. Both roles demand in-depth knowledge of cybersecurity frameworks, threat intelligence, and continuous learning to adapt to evolving cyber threats.
Certification and Training Paths
Ethical hackers commonly pursue certifications such as CEH (Certified Ethical Hacker) and OSCP (Offensive Security Certified Professional) to validate their skills in identifying vulnerabilities and simulating cyber-attacks. Penetration testers often focus on advanced training through OSCP, OSCE (Offensive Security Certified Expert), and GPEN (GIAC Penetration Tester), emphasizing hands-on experience in exploiting systems and comprehensive security assessments. Both roles require continuous education and practical labs, but penetration testers generally have deeper specialization in exploitation techniques and report writing.
Tools and Techniques Used
Ethical hackers utilize a broad range of tools including Metasploit, Nmap, and Wireshark to simulate real-world cyber attacks, identifying vulnerabilities with tactics such as social engineering and network scanning. Penetration testers often employ automated vulnerability scanners like Nessus and Burp Suite alongside manual exploitation methods to rigorously assess system defenses. Both roles emphasize different approaches to security testing, where ethical hackers simulate attacks to expose weaknesses, while penetration testers validate the effectiveness of existing security measures through systematic evaluation.
Real-World Applications and Scenarios
Ethical hackers simulate cyberattacks to identify vulnerabilities before malicious actors exploit them, often working in diverse environments such as financial institutions, healthcare, and government agencies to safeguard sensitive data. Penetration testers specialize in controlled, systematic testing of specific systems or applications, providing detailed reports that guide remediation efforts in development and production stages. Real-world applications highlight that ethical hackers frequently engage in continuous security assessments, while penetration testers focus on predefined objectives within scoped environments to ensure compliance and risk management.
Differences in Testing Methodologies
Ethical hackers employ a broad range of techniques, often using social engineering and unconventional tactics to mimic real-world attackers, while penetration testers follow a structured and methodical approach based on predefined scopes and regulations. Penetration testing prioritizes detailed reporting and compliance with industry standards such as OWASP and NIST, ensuring vulnerabilities are documented systematically. Ethical hackers aim to uncover weaknesses beyond technical flaws, including human factors, making their testing methodologies more exploratory and adaptive.
Career Pathways and Advancement
Ethical hackers and penetration testers share overlapping skills in cybersecurity but diverge in career focus and advancement opportunities, with ethical hackers often progressing into roles like security consultants, incident responders, or chief information security officers due to their broader strategic impact. Penetration testers typically advance by specializing in niche areas such as network vulnerabilities, application security, or red teaming, often gaining certifications like OSCP or CEH to enhance credibility and job prospects. Career progression for both roles depends heavily on practical experience, certifications, and continuous learning in evolving threat landscapes.
Salary and Market Demand Comparison
Ethical hackers typically command higher salaries than penetration testers due to their broader skill set and responsibility in proactively identifying security vulnerabilities across complex systems. Market demand for ethical hackers is growing rapidly, driven by increasing cyber threats and regulatory compliance requirements, with average salaries ranging from $85,000 to $130,000 annually compared to penetration testers, who earn between $70,000 and $110,000. Organizations prioritize ethical hackers for strategic security insights, boosting their demand in sectors like finance, healthcare, and government.
How to Choose the Right Role for You
Choosing between an ethical hacker and a penetration tester depends on your career goals and skill set; ethical hackers focus on proactive security measures by identifying vulnerabilities through creative hacking techniques, while penetration testers systematically assess security by simulating attacks within defined parameters. Evaluate your preference for hands-on, real-time problem solving versus structured, methodical security analysis to align with the role that best fits your strengths. Consider certifications like CEH for ethical hacking and OSCP for penetration testing to complement your chosen career path in cybersecurity.
Ethical Hacker vs Penetration Tester Infographic
 jobdiv.com
jobdiv.com