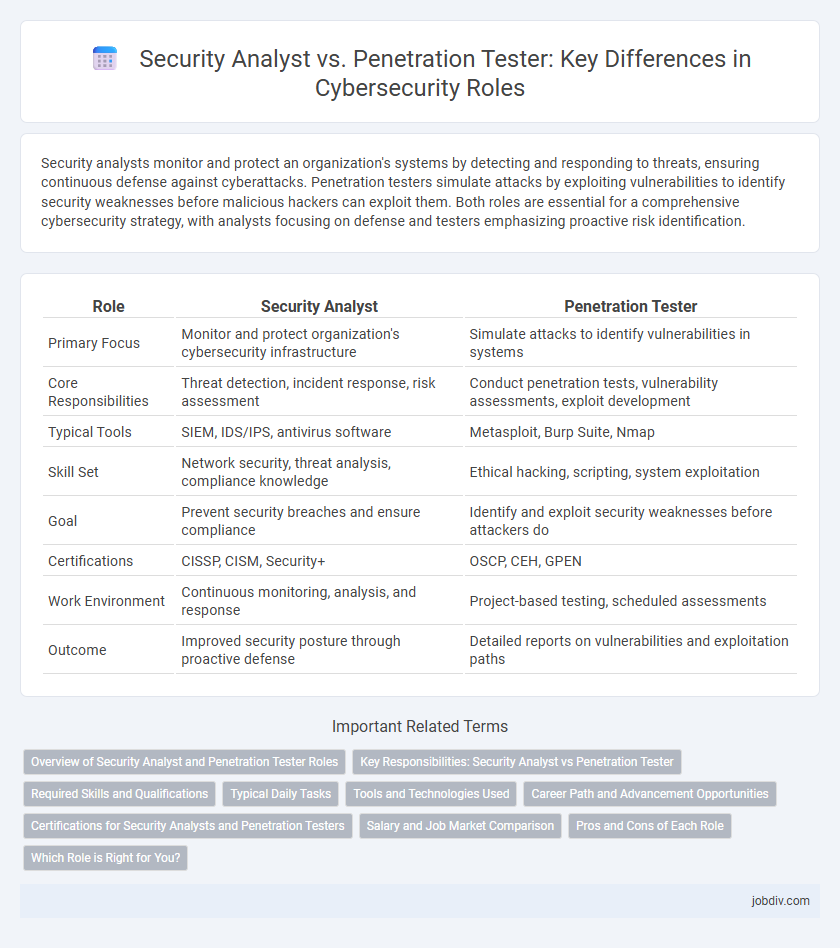
Security analysts monitor and protect an organization's systems by detecting and responding to threats, ensuring continuous defense against cyberattacks. Penetration testers simulate attacks by exploiting vulnerabilities to identify security weaknesses before malicious hackers can exploit them. Both roles are essential for a comprehensive cybersecurity strategy, with analysts focusing on defense and testers emphasizing proactive risk identification.
Table of Comparison
| Role | Security Analyst | Penetration Tester |
|---|---|---|
| Primary Focus | Monitor and protect organization's cybersecurity infrastructure | Simulate attacks to identify vulnerabilities in systems |
| Core Responsibilities | Threat detection, incident response, risk assessment | Conduct penetration tests, vulnerability assessments, exploit development |
| Typical Tools | SIEM, IDS/IPS, antivirus software | Metasploit, Burp Suite, Nmap |
| Skill Set | Network security, threat analysis, compliance knowledge | Ethical hacking, scripting, system exploitation |
| Goal | Prevent security breaches and ensure compliance | Identify and exploit security weaknesses before attackers do |
| Certifications | CISSP, CISM, Security+ | OSCP, CEH, GPEN |
| Work Environment | Continuous monitoring, analysis, and response | Project-based testing, scheduled assessments |
| Outcome | Improved security posture through proactive defense | Detailed reports on vulnerabilities and exploitation paths |
Overview of Security Analyst and Penetration Tester Roles
Security Analysts monitor and protect an organization's IT infrastructure by detecting vulnerabilities and responding to security incidents, often using tools like SIEM and intrusion detection systems. Penetration Testers simulate cyberattacks to identify exploitable weaknesses, leveraging techniques such as ethical hacking and vulnerability assessments. Both roles require strong knowledge of cybersecurity frameworks, but Security Analysts focus on ongoing defense mechanisms while Penetration Testers emphasize proactive threat simulation.
Key Responsibilities: Security Analyst vs Penetration Tester
Security analysts continuously monitor and assess an organization's security posture, investigate security incidents, and implement protective measures to prevent cyber threats. Penetration testers simulate cyberattacks by exploiting vulnerabilities in systems, networks, and applications to identify security weaknesses before malicious actors can. Both roles crucially contribute to cybersecurity, with analysts emphasizing defense strategies and testers focusing on offensive security assessments.
Required Skills and Qualifications
A Security Analyst requires strong knowledge of network security, threat analysis, and incident response, along with proficiency in security information and event management (SIEM) tools and vulnerability assessment. Penetration Testers must possess advanced skills in ethical hacking, exploit development, and familiarity with tools such as Metasploit, Burp Suite, and Kali Linux, paired with certifications like CEH or OSCP. Both roles demand a solid understanding of cybersecurity principles, but penetration testers emphasize offensive techniques, whereas security analysts focus on monitoring and defending systems.
Typical Daily Tasks
Security analysts monitor networks and systems continuously to detect and respond to security incidents, manage firewalls, and analyze security alerts. Penetration testers simulate cyberattacks by identifying vulnerabilities through controlled exploits, conducting security assessments, and reporting weaknesses for remediation. Both roles require extensive knowledge of cybersecurity tools, but security analysts emphasize real-time defense while penetration testers focus on proactive vulnerability identification.
Tools and Technologies Used
Security analysts leverage tools like SIEM platforms (Splunk, QRadar) and endpoint detection systems to monitor, detect, and respond to cyber threats in real time. Penetration testers use specialized tools such as Metasploit, Burp Suite, and Nmap to simulate attacks and identify vulnerabilities in networks and applications. Both roles require proficiency with scripting languages and vulnerability assessment technologies to enhance cybersecurity defenses effectively.
Career Path and Advancement Opportunities
Security analysts focus on monitoring and preventing security breaches by analyzing threats and implementing safeguards, often progressing to roles like security manager or chief information security officer (CISO). Penetration testers specialize in identifying vulnerabilities through simulated attacks, with advancement opportunities leading to senior ethical hacker, security consultant, or cybersecurity architect positions. Both career paths offer growth potential in cybersecurity, but penetration testers typically engage more directly with offensive security techniques, while security analysts emphasize defensive strategies and risk management.
Certifications for Security Analysts and Penetration Testers
Security Analysts often pursue certifications such as CompTIA Security+, Certified Information Systems Security Professional (CISSP), and Certified Information Security Manager (CISM) to validate their skills in risk management and incident response. Penetration Testers typically obtain Offensive Security Certified Professional (OSCP), Certified Ethical Hacker (CEH), and GIAC Penetration Tester (GPEN) certifications to demonstrate expertise in vulnerability assessment and ethical hacking techniques. These certification paths highlight the distinct yet complementary skill sets required for defense-oriented monitoring versus offensive security testing roles.
Salary and Job Market Comparison
Security Analysts typically earn an average salary ranging from $70,000 to $95,000 annually, while Penetration Testers command higher salaries, often between $85,000 and $120,000, reflecting their specialized skills in ethical hacking. The job market for Security Analysts is broader, with increasing demand across various industries for threat detection and risk management, whereas Penetration Testers are sought after primarily by organizations prioritizing proactive vulnerability assessments. Both roles experience strong employment growth driven by escalating cybersecurity threats and evolving regulatory requirements.
Pros and Cons of Each Role
Security analysts excel in continuously monitoring systems and identifying vulnerabilities through comprehensive threat analysis, offering a defensive approach that strengthens overall cybersecurity posture; however, their reactive nature may limit exposure to advanced exploitation techniques. Penetration testers specialize in simulating cyberattacks to identify security weaknesses before they are exploited, providing proactive insight into system vulnerabilities, yet their role is often project-based and may lack ongoing monitoring responsibilities. Balancing these roles enhances an organization's defense-in-depth strategy by integrating persistent security oversight with targeted offensive testing.
Which Role is Right for You?
A Security Analyst focuses on monitoring, detecting, and responding to cyber threats by analyzing security systems and implementing protective measures, making it ideal for individuals who enjoy continuous risk assessment and incident management. A Penetration Tester, on the other hand, simulates cyberattacks to identify vulnerabilities in networks and software, suited for those who prefer hands-on ethical hacking and proactive threat identification. Choosing the right role depends on whether you are more interested in defending systems through analysis or actively testing their defenses through simulated attacks.
Security Analyst vs Penetration Tester Infographic
 jobdiv.com
jobdiv.com