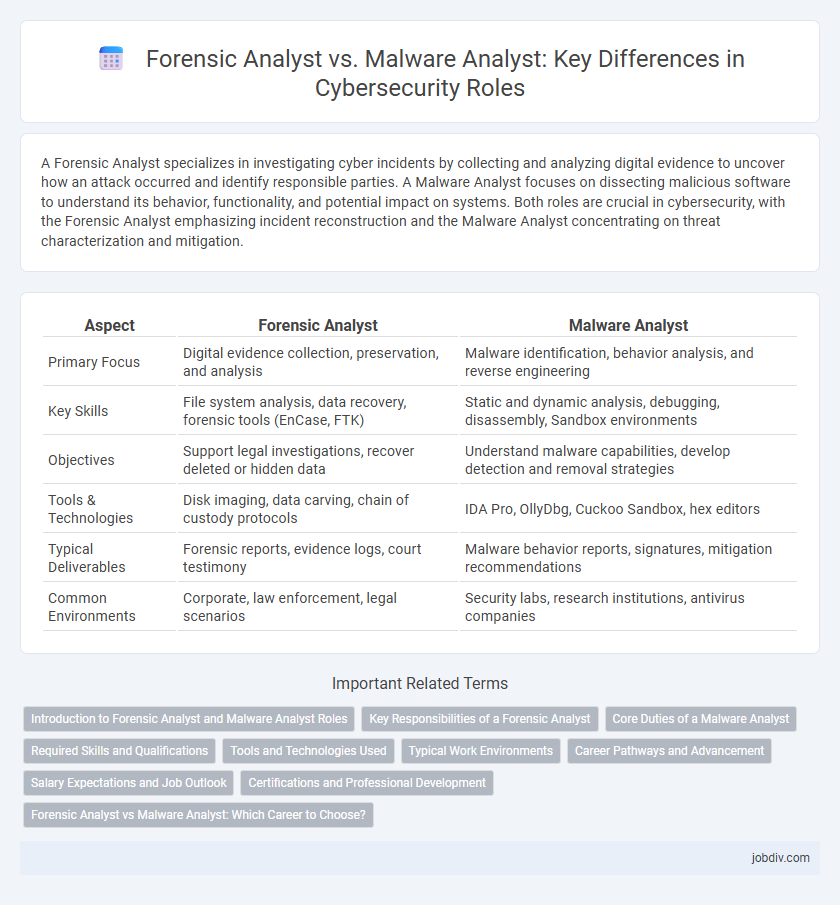
A Forensic Analyst specializes in investigating cyber incidents by collecting and analyzing digital evidence to uncover how an attack occurred and identify responsible parties. A Malware Analyst focuses on dissecting malicious software to understand its behavior, functionality, and potential impact on systems. Both roles are crucial in cybersecurity, with the Forensic Analyst emphasizing incident reconstruction and the Malware Analyst concentrating on threat characterization and mitigation.
Table of Comparison
| Aspect | Forensic Analyst | Malware Analyst |
|---|---|---|
| Primary Focus | Digital evidence collection, preservation, and analysis | Malware identification, behavior analysis, and reverse engineering |
| Key Skills | File system analysis, data recovery, forensic tools (EnCase, FTK) | Static and dynamic analysis, debugging, disassembly, Sandbox environments |
| Objectives | Support legal investigations, recover deleted or hidden data | Understand malware capabilities, develop detection and removal strategies |
| Tools & Technologies | Disk imaging, data carving, chain of custody protocols | IDA Pro, OllyDbg, Cuckoo Sandbox, hex editors |
| Typical Deliverables | Forensic reports, evidence logs, court testimony | Malware behavior reports, signatures, mitigation recommendations |
| Common Environments | Corporate, law enforcement, legal scenarios | Security labs, research institutions, antivirus companies |
Introduction to Forensic Analyst and Malware Analyst Roles
Forensic analysts specialize in examining digital evidence from cyber incidents, using tools to recover and analyze data from compromised systems to support investigations. Malware analysts focus on dissecting malicious software to understand its behavior, origin, and impact, enabling the creation of effective countermeasures and threat intelligence. Both roles require expertise in cybersecurity principles, but forensic analysts emphasize incident reconstruction while malware analysts concentrate on reverse engineering and malware taxonomy.
Key Responsibilities of a Forensic Analyst
A Forensic Analyst is responsible for collecting, preserving, and analyzing digital evidence from computers, networks, and storage devices to support investigations and legal proceedings. They perform data recovery, trace cyber intrusions, and create detailed reports to help law enforcement agencies and organizations understand the scope and impact of security incidents. Their work ensures the integrity and admissibility of digital evidence while aiding in the identification of threat actors and attack methodologies.
Core Duties of a Malware Analyst
Malware Analysts specialize in identifying, dissecting, and understanding malicious software to determine its origin, functionality, and potential impact on systems. Core duties include reverse engineering malware code, analyzing threat behaviors, mapping infection vectors, and developing detection signatures for security tools. Their work supports incident response teams by providing detailed threat intelligence and enabling proactive defense mechanisms against evolving cyber threats.
Required Skills and Qualifications
Forensic Analysts require expertise in digital evidence preservation, chain of custody procedures, and proficiency with forensic tools like EnCase and FTK, alongside certifications such as CFCE or GCFA. Malware Analysts must possess strong programming skills in languages like C/C++ and Python, deep understanding of assembly language, reverse engineering, and experience with debugging tools such as IDA Pro or Ghidra, often holding certifications like GREM or CEH. Both roles demand critical thinking, attention to detail, and knowledge of cybersecurity principles, but Forensic Analysts focus on post-incident investigation while Malware Analysts specialize in identifying and mitigating malicious code.
Tools and Technologies Used
Forensic analysts utilize tools like EnCase, FTK, and Autopsy for data recovery, file integrity verification, and timeline reconstruction during investigations. Malware analysts rely on technologies such as IDA Pro, OllyDbg, and sandbox environments like Cuckoo to dissect malicious code and understand its behavior. Both roles leverage advanced forensic and reverse engineering software to support thorough analysis and incident response.
Typical Work Environments
Forensic analysts typically work in law enforcement agencies, cybersecurity firms, or corporate security departments, focusing on investigating cybercrimes by examining digital evidence in controlled lab environments. Malware analysts often operate within threat intelligence teams or software security companies, analyzing malicious code in isolated sandbox environments to understand and mitigate cyber threats. Both roles require secure, access-controlled settings to handle sensitive data and maintain chain-of-custody protocols.
Career Pathways and Advancement
Forensic Analysts specialize in investigating cybercrime through digital evidence recovery and analysis, progressing into roles such as Cybersecurity Consultant or Incident Response Manager. Malware Analysts focus on dissecting malicious software to understand attack vectors and develop defenses, often advancing to positions like Threat Intelligence Analyst or Malware Researcher. Both career paths require strong analytical skills and offer opportunities in cybersecurity firms, law enforcement agencies, and government organizations with increasing responsibilities in threat mitigation and cyber defense strategy.
Salary Expectations and Job Outlook
Forensic Analysts typically earn an average salary ranging from $65,000 to $95,000 annually, reflecting their role in investigating digital crimes and recovering evidence. Malware Analysts command salaries between $75,000 and $110,000, driven by their expertise in identifying and neutralizing malicious software threats. Both positions offer strong job growth, with Malware Analysts experiencing higher demand due to increasing cyberattack complexity and the need for advanced threat detection.
Certifications and Professional Development
Forensic Analysts commonly pursue certifications such as Certified Computer Examiner (CCE) and GIAC Certified Forensic Analyst (GCFA) to demonstrate expertise in digital evidence collection and analysis. Malware Analysts often obtain credentials like GIAC Reverse Engineering Malware (GREM) and Offensive Security Certified Expert (OSCE) to validate skills in dissecting and understanding malicious code. Continuous professional development through workshops, industry conferences, and specialized training is essential for both roles to stay current with evolving cyber threats and forensic technologies.
Forensic Analyst vs Malware Analyst: Which Career to Choose?
Forensic Analysts specialize in investigating cybercrime by collecting and analyzing digital evidence to support legal proceedings, focusing on data recovery and incident reconstruction. Malware Analysts concentrate on identifying, dissecting, and understanding malicious software to develop defense mechanisms and improve threat detection. Choosing between these careers depends on your interest in either legal investigative processes or technical reverse engineering and threat mitigation within cybersecurity.
Forensic Analyst vs Malware Analyst Infographic
 jobdiv.com
jobdiv.com