A Security Consultant develops tailored strategies to protect an organization's assets by assessing risks and recommending proactive measures. A Security Auditor systematically evaluates existing security controls to ensure compliance with established standards and identify vulnerabilities. Both roles are critical for comprehensive security management, with consultants focusing on prevention and auditors emphasizing verification.
Table of Comparison
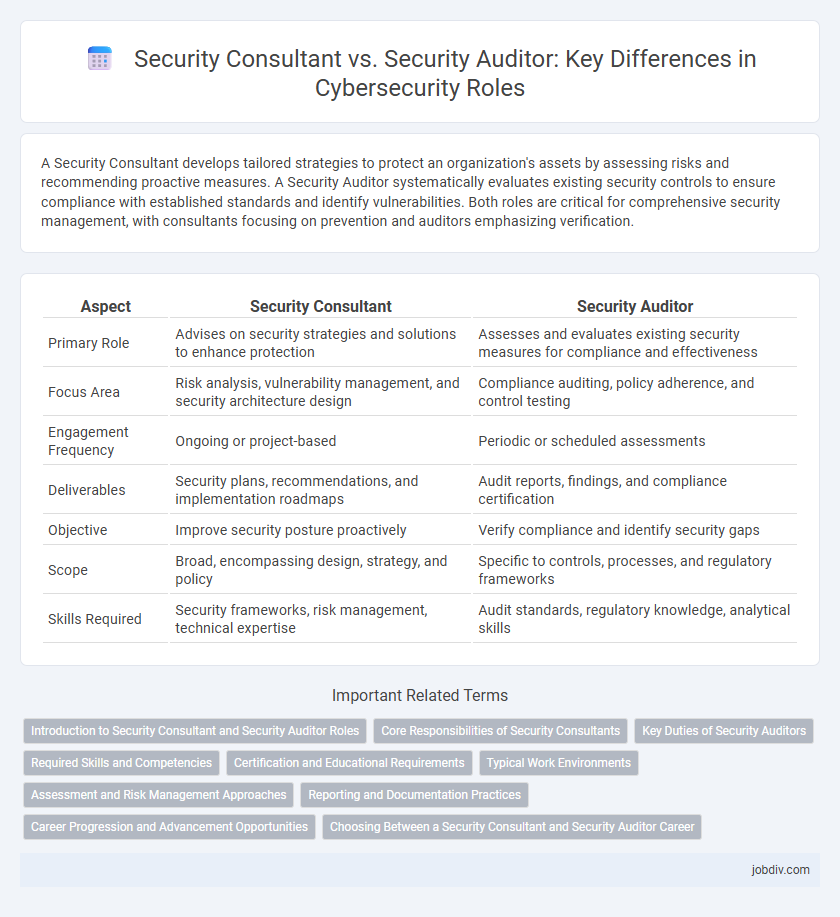
| Aspect | Security Consultant | Security Auditor |
|---|---|---|
| Primary Role | Advises on security strategies and solutions to enhance protection | Assesses and evaluates existing security measures for compliance and effectiveness |
| Focus Area | Risk analysis, vulnerability management, and security architecture design | Compliance auditing, policy adherence, and control testing |
| Engagement Frequency | Ongoing or project-based | Periodic or scheduled assessments |
| Deliverables | Security plans, recommendations, and implementation roadmaps | Audit reports, findings, and compliance certification |
| Objective | Improve security posture proactively | Verify compliance and identify security gaps |
| Scope | Broad, encompassing design, strategy, and policy | Specific to controls, processes, and regulatory frameworks |
| Skills Required | Security frameworks, risk management, technical expertise | Audit standards, regulatory knowledge, analytical skills |
Introduction to Security Consultant and Security Auditor Roles
Security consultants provide expert guidance on designing, implementing, and maintaining an organization's security infrastructure to protect against cyber threats and vulnerabilities. Security auditors systematically evaluate and verify the effectiveness of existing security measures, compliance with policies, and regulatory standards through detailed assessments and reporting. Both roles are critical for comprehensive risk management, with consultants focusing on proactive security strategies and auditors concentrating on compliance and control validation.
Core Responsibilities of Security Consultants
Security consultants specialize in assessing organizational vulnerabilities, designing tailored security frameworks, and implementing proactive measures to prevent cyber threats. Their core responsibilities include conducting risk analyses, advising on regulatory compliance, and developing strategic security plans aligned with business objectives. Unlike security auditors who focus on evaluating and reporting compliance adherence, consultants provide ongoing guidance and practical solutions to enhance overall security posture.
Key Duties of Security Auditors
Security auditors primarily conduct comprehensive assessments of organizational security policies, procedures, and controls to ensure compliance with industry standards and regulatory requirements. They perform detailed risk analyses and vulnerability assessments to identify potential security gaps and recommend corrective actions. Their duties include preparing audit reports that document findings, non-compliance issues, and suggest improvements to strengthen overall security posture.
Required Skills and Competencies
Security Consultants require strong expertise in risk assessment, threat modeling, and designing tailored security solutions to protect organizational assets effectively. Security Auditors need proficiency in compliance standards, audit methodologies, and vulnerability assessment to evaluate and ensure adherence to security policies and regulatory requirements. Both roles demand analytical thinking, attention to detail, and thorough knowledge of cybersecurity frameworks such as ISO 27001, NIST, and GDPR.
Certification and Educational Requirements
Security Consultants typically require certifications such as CISSP, CISM, or CEH to demonstrate expertise in risk assessment and security strategy implementation, complemented by a bachelor's degree in cybersecurity, information technology, or related fields. Security Auditors often hold certifications like CISA or ISO 27001 Lead Auditor, emphasizing skills in compliance assessment and audit processes, alongside educational backgrounds in accounting, information systems, or cybersecurity. Both roles benefit from continuous professional development, but Security Auditors focus more on regulatory standards and audit methodologies, while Consultants prioritize comprehensive security frameworks and threat management.
Typical Work Environments
Security Consultants typically operate within diverse environments including corporate offices, government agencies, and cybersecurity firms, providing tailored risk assessments and strategic security solutions. Security Auditors mainly work in regulated industries such as finance, healthcare, and manufacturing, performing compliance checks and vulnerability assessments to ensure adherence to security policies and standards. Both roles often require collaboration with IT departments and management teams in onsite or remote settings to enhance organizational security posture.
Assessment and Risk Management Approaches
Security consultants perform comprehensive risk assessments by identifying vulnerabilities and recommending tailored mitigation strategies to enhance organizational security posture. Security auditors systematically evaluate compliance with established security policies and regulatory requirements through detailed audits and control reviews. Both roles employ distinct assessment methodologies, with consultants emphasizing proactive risk management and auditors focusing on verifying adherence to standards.
Reporting and Documentation Practices
Security Consultants develop comprehensive security strategies and deliver detailed reports tailored to organizational needs, emphasizing actionable recommendations and risk mitigation plans. Security Auditors concentrate on evaluating compliance with established standards, producing audit reports that document findings, control gaps, and adherence to regulatory requirements. Effective reporting from both roles ensures clear documentation of security posture, facilitating informed decision-making and continuous improvement.
Career Progression and Advancement Opportunities
Security Consultants typically leverage their expertise to design and implement comprehensive security strategies, positioning themselves for leadership roles such as Chief Information Security Officer (CISO) or Security Director. Security Auditors, with their strong focus on compliance and risk assessment, often advance into specialized roles like Compliance Manager or Risk Analyst before transitioning into broader cybersecurity management positions. Both career paths offer opportunities for growth, but consultants usually experience faster progression into strategic roles due to their client-facing and solution-driven responsibilities.
Choosing Between a Security Consultant and Security Auditor Career
Choosing between a career as a Security Consultant and a Security Auditor depends on your preference for proactive versus evaluative roles in cybersecurity. Security Consultants design and implement tailored security strategies, requiring strong problem-solving skills and client collaboration, while Security Auditors focus on compliance assessments and identifying vulnerabilities through systematic audits. Understanding industry demand highlights that consultants often engage in dynamic, project-based environments, whereas auditors provide critical assurance to organizations by ensuring regulatory adherence and risk mitigation.
Security Consultant vs Security Auditor Infographic
 jobdiv.com
jobdiv.com