Physical security protects pets by preventing unauthorized access through locks, barriers, and surveillance, ensuring their safety at home. Digital security safeguards pet monitoring devices, such as GPS trackers and cameras, from hacking or data breaches that could compromise pet location and owner privacy. Combining both physical and digital security measures creates a comprehensive defense system to keep pets safe and secure.
Table of Comparison
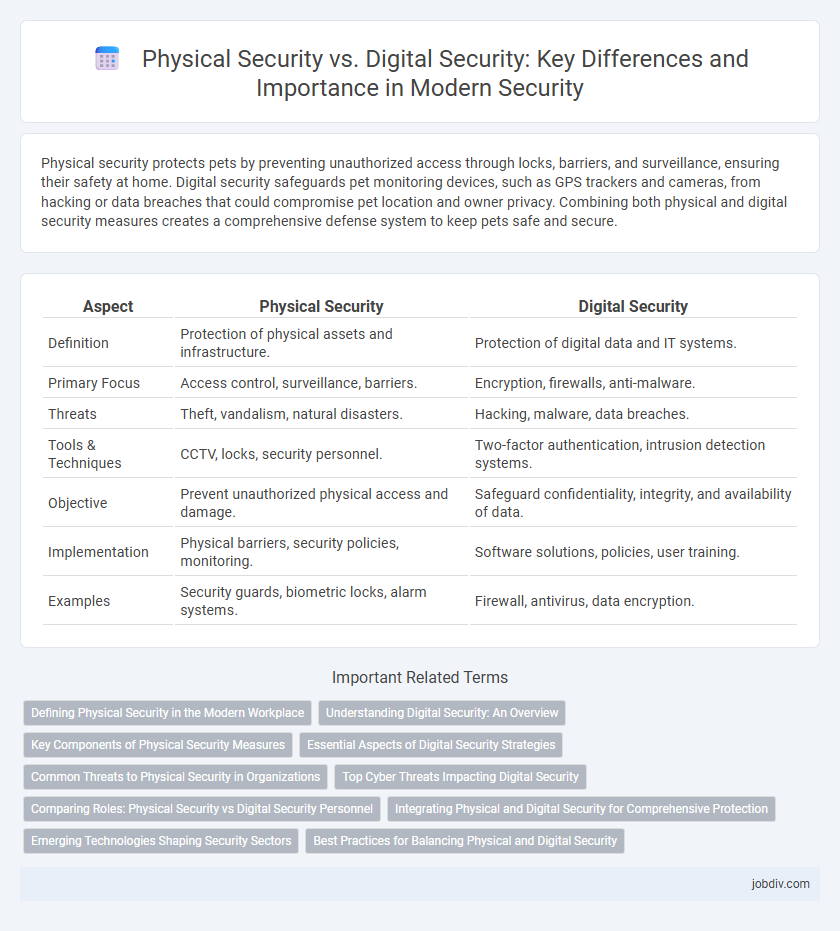
| Aspect | Physical Security | Digital Security |
|---|---|---|
| Definition | Protection of physical assets and infrastructure. | Protection of digital data and IT systems. |
| Primary Focus | Access control, surveillance, barriers. | Encryption, firewalls, anti-malware. |
| Threats | Theft, vandalism, natural disasters. | Hacking, malware, data breaches. |
| Tools & Techniques | CCTV, locks, security personnel. | Two-factor authentication, intrusion detection systems. |
| Objective | Prevent unauthorized physical access and damage. | Safeguard confidentiality, integrity, and availability of data. |
| Implementation | Physical barriers, security policies, monitoring. | Software solutions, policies, user training. |
| Examples | Security guards, biometric locks, alarm systems. | Firewall, antivirus, data encryption. |
Defining Physical Security in the Modern Workplace
Physical security in the modern workplace encompasses measures such as access control systems, surveillance cameras, and security personnel to protect employees, assets, and sensitive information from unauthorized physical access, theft, or damage. It involves securing entry points, monitoring environments, and implementing protocols to mitigate risks related to vandalism, natural disasters, and workplace violence. Integrating physical security with digital security systems enhances overall protection by creating a comprehensive defense strategy against both physical and cyber threats.
Understanding Digital Security: An Overview
Digital security involves protecting data, networks, and systems from cyber threats such as hacking, malware, and unauthorized access. It encompasses encryption, multi-factor authentication, and regular software updates to safeguard sensitive information and maintain system integrity. Effective digital security strategies are essential to prevent data breaches, ensure privacy, and maintain continuous business operations in a connected world.
Key Components of Physical Security Measures
Key components of physical security measures include access control systems, surveillance cameras, security guards, and environmental design. Access control systems utilize biometric scanners, keycards, or PINs to restrict unauthorized entry, while surveillance cameras provide continuous monitoring and recording of sensitive areas. Security guards offer real-time response and deterrence, and environmental design such as barriers, lighting, and secure locks enhances the physical protection of assets and personnel.
Essential Aspects of Digital Security Strategies
Digital security strategies prioritize robust encryption protocols, multi-factor authentication, and continuous network monitoring to safeguard sensitive information from cyber threats. Implementing real-time threat detection systems and regular security audits enhances resilience against data breaches and unauthorized access. Emphasizing employee cybersecurity training and incident response plans further strengthens an organization's defense against evolving digital attacks.
Common Threats to Physical Security in Organizations
Common threats to physical security in organizations include unauthorized access, theft, vandalism, and workplace violence, which compromise employee safety and asset protection. Tailgating, social engineering, and insider threats pose significant risks by bypassing security controls or exploiting human vulnerabilities. Effective physical security strategies integrate access control systems, surveillance cameras, and security personnel to mitigate these risks and safeguard organizational infrastructure.
Top Cyber Threats Impacting Digital Security
Top cyber threats impacting digital security include ransomware, phishing attacks, and data breaches targeting sensitive information in corporate networks and cloud environments. Advanced Persistent Threats (APTs) exploit vulnerabilities to maintain prolonged access, compromising organizational assets and user privacy. Implementing multi-factor authentication, continuous monitoring, and regular software updates significantly mitigates these cyber risks.
Comparing Roles: Physical Security vs Digital Security Personnel
Physical security personnel safeguard tangible assets such as buildings, equipment, and personnel by implementing access controls, surveillance systems, and emergency response measures. Digital security personnel focus on protecting information systems, networks, and data from cyber threats through activities like threat monitoring, vulnerability assessment, and incident response. Both roles require specialized skills but address different threat landscapes to ensure comprehensive organizational protection.
Integrating Physical and Digital Security for Comprehensive Protection
Integrating physical security measures such as access control systems, surveillance cameras, and security personnel with digital security protocols including firewalls, encryption, and multi-factor authentication ensures a comprehensive protection framework. Combining these strategies mitigates risks from both physical breaches and cyber threats, addressing vulnerabilities that could be exploited in isolation. Organizations implementing convergence of security technologies can enhance real-time threat detection, response capabilities, and overall resilience.
Emerging Technologies Shaping Security Sectors
Emerging technologies such as artificial intelligence, biometric authentication, and the Internet of Things (IoT) are revolutionizing both physical and digital security sectors by enabling real-time threat detection and response. Advanced surveillance systems integrating AI-powered video analytics enhance physical security by identifying suspicious activities with greater accuracy, while blockchain technology strengthens digital security through decentralized and tamper-proof transaction records. The convergence of these innovations facilitates a comprehensive security framework that addresses vulnerabilities across physical access points and cyber infrastructures.
Best Practices for Balancing Physical and Digital Security
Effective balancing of physical and digital security involves integrating access control systems with cybersecurity protocols to prevent unauthorized entry and data breaches. Regularly updating security hardware, such as surveillance cameras and biometric scanners, complements strong password policies and multi-factor authentication to protect sensitive information. Conducting comprehensive risk assessments helps organizations identify vulnerabilities in both physical premises and digital infrastructure, enabling targeted security measures that enhance overall protection.
Physical Security vs Digital Security Infographic
 jobdiv.com
jobdiv.com