SOC Analysts monitor security systems and alerts to detect and respond to potential threats in real-time, ensuring continuous protection against cyberattacks. Threat Hunters proactively search for hidden threats and vulnerabilities by analyzing data patterns and unusual behaviors that evade automated detection tools. Both roles are crucial for a comprehensive cybersecurity strategy, combining immediate incident response with deep investigative expertise.
Table of Comparison
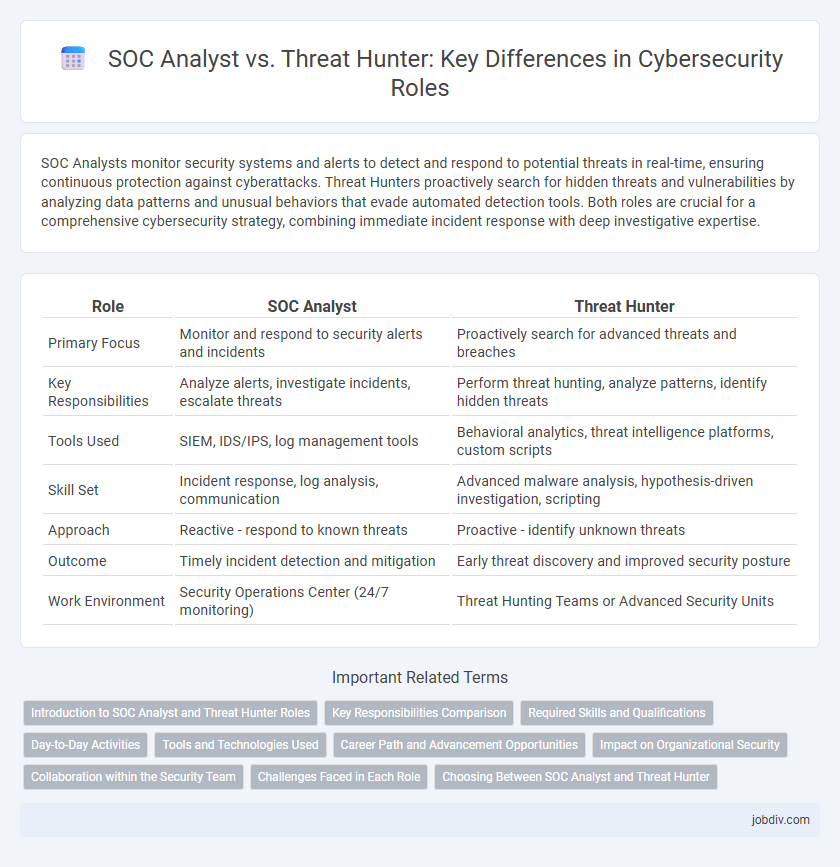
| Role | SOC Analyst | Threat Hunter |
|---|---|---|
| Primary Focus | Monitor and respond to security alerts and incidents | Proactively search for advanced threats and breaches |
| Key Responsibilities | Analyze alerts, investigate incidents, escalate threats | Perform threat hunting, analyze patterns, identify hidden threats |
| Tools Used | SIEM, IDS/IPS, log management tools | Behavioral analytics, threat intelligence platforms, custom scripts |
| Skill Set | Incident response, log analysis, communication | Advanced malware analysis, hypothesis-driven investigation, scripting |
| Approach | Reactive - respond to known threats | Proactive - identify unknown threats |
| Outcome | Timely incident detection and mitigation | Early threat discovery and improved security posture |
| Work Environment | Security Operations Center (24/7 monitoring) | Threat Hunting Teams or Advanced Security Units |
Introduction to SOC Analyst and Threat Hunter Roles
SOC Analysts monitor security systems, analyze alerts, and respond to incidents to maintain organizational cybersecurity. Threat Hunters proactively search for hidden threats and advanced persistent threats (APTs) using behavioral analysis and threat intelligence. Both roles collaborate to enhance threat detection, leveraging tools like SIEM and EDR for comprehensive security posture.
Key Responsibilities Comparison
SOC Analysts primarily monitor security alerts, analyze incidents, and manage response protocols to maintain organizational cybersecurity. Threat Hunters proactively search for hidden threats by leveraging advanced threat intelligence and behavioral analysis to identify and mitigate sophisticated attacks. Both roles require expertise in cybersecurity tools and techniques, but SOC Analysts focus on reactive incident management, while Threat Hunters emphasize proactive threat detection.
Required Skills and Qualifications
SOC Analysts require strong proficiency in incident detection, log analysis, and familiarity with SIEM tools such as Splunk or QRadar, combined with certifications like CompTIA Security+ or CEH. Threat Hunters must possess advanced skills in behavioral analysis, hypothesis-driven investigations, and deep knowledge of malware, APT tactics, and threat intelligence platforms, often supported by certifications like GIAC Cyber Threat Intelligence (GCTI) or Certified Threat Intelligence Analyst (CTIA). Both roles demand solid understanding of networking, operating systems, and scripting languages such as Python or PowerShell for effective cyber defense.
Day-to-Day Activities
SOC Analysts monitor security alerts, investigate incidents, and respond to threats by following established protocols to ensure system integrity. Threat Hunters proactively search for hidden threats by analyzing anomalous behavior and leveraging advanced threat intelligence tools to identify vulnerabilities. Both roles require continuous collaboration to enhance an organization's overall cybersecurity posture through real-time detection and proactive threat mitigation.
Tools and Technologies Used
SOC Analysts primarily rely on Security Information and Event Management (SIEM) systems like Splunk, IBM QRadar, and ArcSight to aggregate and analyze security alerts, alongside endpoint detection and response (EDR) tools such as CrowdStrike and Carbon Black to monitor and respond to incidents in real-time. Threat Hunters utilize advanced threat intelligence platforms like Mandiant and Recorded Future, along with behavioral analytics tools and custom scripts in Python or PowerShell to proactively identify sophisticated threats hidden within network and system data. Both roles leverage network traffic analysis tools such as Wireshark and Zeek, but Threat Hunters often focus more on anomaly detection frameworks and machine learning-based solutions for deep investigation beyond automated alerts.
Career Path and Advancement Opportunities
SOC Analysts typically start with foundational skills in monitoring and incident response, advancing by gaining certifications such as CompTIA Security+ or CISSP to move into senior analyst or managerial roles. Threat Hunters often require advanced expertise in threat intelligence and malware analysis, progressing towards specialized positions like Threat Intelligence Lead or cybersecurity architect. Career advancement in both roles benefits from continuous learning and hands-on experience with emerging security technologies and attack methodologies.
Impact on Organizational Security
SOC Analysts monitor and respond to security incidents in real-time, minimizing damage and ensuring swift remediation to protect organizational assets. Threat Hunters proactively search for hidden threats and advanced persistent threats (APTs) that evade automated defenses, enhancing the organization's long-term security posture. Together, these roles create a comprehensive defense strategy, combining immediate incident response with strategic threat detection to reduce risk and improve resilience.
Collaboration within the Security Team
SOC analysts and threat hunters play complementary roles in cybersecurity, fostering effective collaboration within the security team by sharing real-time threat intelligence and incident data. SOC analysts monitor security systems for alerts, while threat hunters proactively seek hidden adversaries using advanced analytics and threat intelligence feeds. This synergy enhances threat detection accuracy, accelerates incident response, and strengthens overall organizational security posture.
Challenges Faced in Each Role
SOC Analysts confront challenges such as managing high volumes of security alerts, ensuring rapid incident response, and maintaining up-to-date knowledge of evolving cyber threats. Threat Hunters face difficulties in proactively detecting sophisticated, stealthy attacks, analyzing large datasets for subtle indicators of compromise, and developing advanced threat detection techniques. Both roles demand continuous learning to adapt to emerging tactics, techniques, and procedures used by adversaries.
Choosing Between SOC Analyst and Threat Hunter
Choosing between a SOC Analyst and a Threat Hunter depends on organizational needs for proactive versus reactive security measures. SOC Analysts monitor, detect, and respond to security incidents in real-time, ensuring immediate threat mitigation and compliance adherence. Threat Hunters specialize in proactively seeking undetected threats through deep analysis and hypothesis-driven investigations to enhance overall threat intelligence and long-term cybersecurity posture.
SOC Analyst vs Threat Hunter Infographic
 jobdiv.com
jobdiv.com