Penetration testing simulates real-world cyberattacks to identify exploitable security weaknesses in a system, providing a detailed report on how hackers could gain unauthorized access. Vulnerability assessment involves scanning and identifying potential security flaws across a network or application without exploiting them, focusing on discovering and prioritizing risks for remediation. Both methods are essential for a comprehensive security pet strategy, with penetration testing offering deeper insights and vulnerability assessment delivering broader vulnerability coverage.
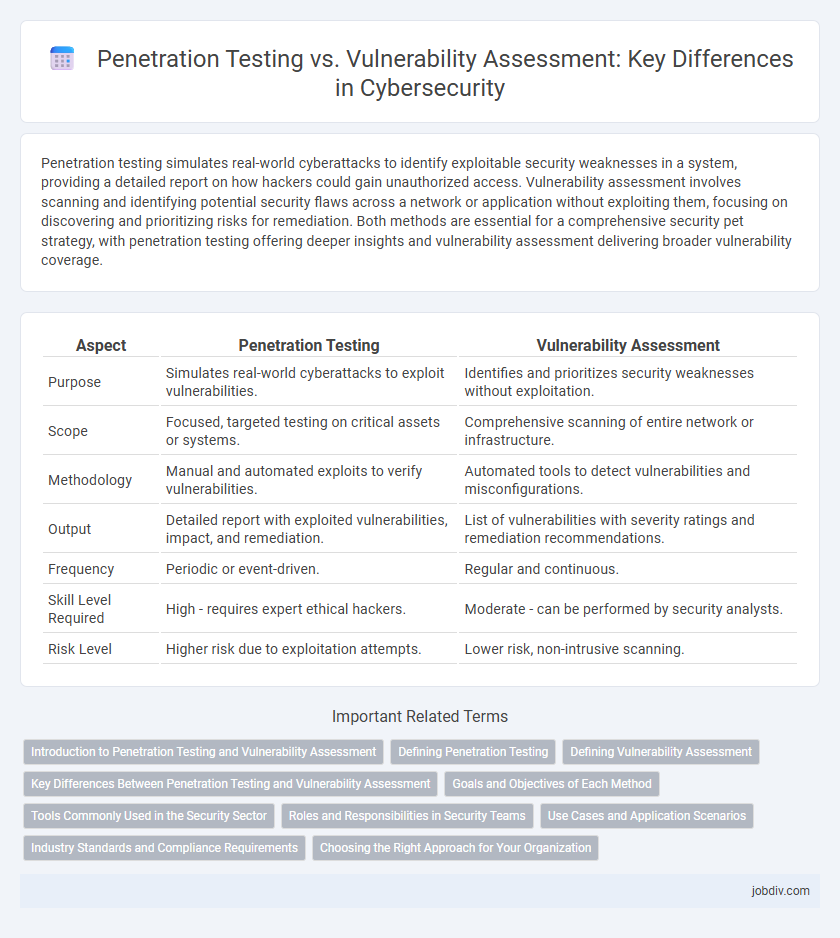
Table of Comparison
| Aspect | Penetration Testing | Vulnerability Assessment |
|---|---|---|
| Purpose | Simulates real-world cyberattacks to exploit vulnerabilities. | Identifies and prioritizes security weaknesses without exploitation. |
| Scope | Focused, targeted testing on critical assets or systems. | Comprehensive scanning of entire network or infrastructure. |
| Methodology | Manual and automated exploits to verify vulnerabilities. | Automated tools to detect vulnerabilities and misconfigurations. |
| Output | Detailed report with exploited vulnerabilities, impact, and remediation. | List of vulnerabilities with severity ratings and remediation recommendations. |
| Frequency | Periodic or event-driven. | Regular and continuous. |
| Skill Level Required | High - requires expert ethical hackers. | Moderate - can be performed by security analysts. |
| Risk Level | Higher risk due to exploitation attempts. | Lower risk, non-intrusive scanning. |
Introduction to Penetration Testing and Vulnerability Assessment
Penetration testing simulates real-world cyberattacks to identify exploitable security weaknesses within systems, networks, or applications by actively exploiting vulnerabilities. Vulnerability assessment systematically scans and analyzes IT environments to detect, classify, and prioritize security flaws without exploiting them. Both methods are essential components of a comprehensive cybersecurity strategy, providing insights to strengthen defenses and reduce risk exposure.
Defining Penetration Testing
Penetration testing involves simulating real-world cyberattacks to identify and exploit vulnerabilities within an organization's network, applications, or systems. This controlled attack method assesses the effectiveness of existing security measures by actively attempting to breach defenses. The goal is to uncover security weaknesses before malicious hackers can exploit them, providing actionable insights to strengthen overall cybersecurity posture.
Defining Vulnerability Assessment
Vulnerability assessment systematically identifies, quantifies, and prioritizes security weaknesses within an organization's IT infrastructure. It involves automated scanning tools and manual analysis to detect vulnerabilities across networks, systems, and applications. The primary goal is to provide actionable insights for risk mitigation before exploitation occurs.
Key Differences Between Penetration Testing and Vulnerability Assessment
Penetration testing simulates real-world cyberattacks to identify exploitable vulnerabilities by actively exploiting security weaknesses, while vulnerability assessment systematically scans and catalogs potential security flaws without exploitation. Penetration tests provide an in-depth analysis of attack paths and impact, emphasizing exploit validation and security control effectiveness. Vulnerability assessments offer comprehensive reports of identified weaknesses, prioritizing risk levels for remediation but lack the detailed attack scenario insights found in penetration testing.
Goals and Objectives of Each Method
Penetration testing aims to simulate real-world cyberattacks to identify exploitable vulnerabilities and assess an organization's security defenses under active threat scenarios. Vulnerability assessment focuses on systematically scanning and cataloging security weaknesses across systems to provide a comprehensive inventory of potential risks without actively exploiting them. The primary objective of penetration testing is to validate the effectiveness of security controls, while vulnerability assessment seeks to prioritize remediation efforts based on identified risk levels.
Tools Commonly Used in the Security Sector
Penetration testing frequently employs tools like Metasploit, Burp Suite, and Nmap to simulate real-world cyberattacks and identify exploitable vulnerabilities. Vulnerability assessments often use scanners such as Nessus, Qualys, and OpenVAS to systematically detect security weaknesses and misconfigurations across networks and systems. Both methods rely on these specialized tools to enhance an organization's security posture through proactive identification and remediation of threats.
Roles and Responsibilities in Security Teams
Penetration testing involves simulating real-world attacks to identify exploitable security weaknesses, typically conducted by specialized ethical hackers or red team members within a security team. Vulnerability assessment focuses on systematically scanning and cataloging security flaws using automated tools, with security analysts or vulnerability management teams prioritizing remediation efforts based on risk severity. While penetration testers actively exploit vulnerabilities to validate risks and test defenses, vulnerability assessors emphasize continuous monitoring and reporting to guide patching and policy improvements.
Use Cases and Application Scenarios
Penetration testing simulates real-world cyberattacks to identify exploitable security flaws, making it ideal for assessing an organization's defense mechanisms and response capabilities. Vulnerability assessment systematically scans and categorizes system weaknesses to provide a comprehensive overview of potential risks, enabling prioritization of remediation efforts. Use cases for penetration testing include critical infrastructure protection and compliance validation, while vulnerability assessments are best suited for routine security maintenance and initial risk evaluation.
Industry Standards and Compliance Requirements
Penetration testing and vulnerability assessment differ significantly in meeting industry standards such as PCI DSS, ISO 27001, and NIST SP 800-115, where penetration testing simulates real-world attacks to identify exploitable security weaknesses, while vulnerability assessments provide a broader insight into potential vulnerabilities through automated scans. Compliance requirements often mandate regular penetration testing to validate the effectiveness of security controls and remediate high-risk issues, whereas vulnerability assessments are typically required more frequently to maintain continuous monitoring and risk management. Integrating both approaches supports comprehensive security strategies that align with regulatory frameworks and reduce the risk of non-compliance penalties.
Choosing the Right Approach for Your Organization
Penetration testing simulates real-world cyberattacks to identify exploitable vulnerabilities, providing in-depth insights into security weaknesses and potential breach impacts. Vulnerability assessments offer a comprehensive scan for known security flaws, enabling organizations to prioritize and remediate risks more efficiently. Selecting the right approach depends on factors like organizational size, compliance requirements, risk tolerance, and available resources to ensure optimal cybersecurity posture.
Penetration Testing vs Vulnerability Assessment Infographic
 jobdiv.com
jobdiv.com