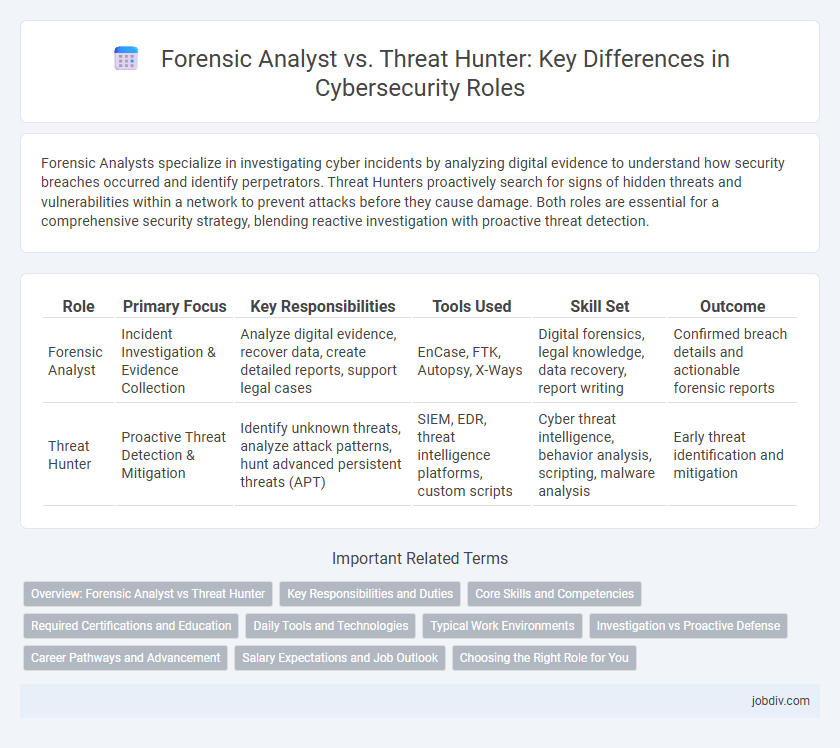
Forensic Analysts specialize in investigating cyber incidents by analyzing digital evidence to understand how security breaches occurred and identify perpetrators. Threat Hunters proactively search for signs of hidden threats and vulnerabilities within a network to prevent attacks before they cause damage. Both roles are essential for a comprehensive security strategy, blending reactive investigation with proactive threat detection.
Table of Comparison
| Role | Primary Focus | Key Responsibilities | Tools Used | Skill Set | Outcome |
|---|---|---|---|---|---|
| Forensic Analyst | Incident Investigation & Evidence Collection | Analyze digital evidence, recover data, create detailed reports, support legal cases | EnCase, FTK, Autopsy, X-Ways | Digital forensics, legal knowledge, data recovery, report writing | Confirmed breach details and actionable forensic reports |
| Threat Hunter | Proactive Threat Detection & Mitigation | Identify unknown threats, analyze attack patterns, hunt advanced persistent threats (APT) | SIEM, EDR, threat intelligence platforms, custom scripts | Cyber threat intelligence, behavior analysis, scripting, malware analysis | Early threat identification and mitigation |
Overview: Forensic Analyst vs Threat Hunter
Forensic analysts specialize in investigating cyber incidents by collecting and analyzing digital evidence to reconstruct attack timelines and identify perpetrators, ensuring legal admissibility. Threat hunters proactively search for hidden threats and indicators of compromise within networks using behavioral analysis and threat intelligence to detect advanced persistent threats before damage occurs. Both roles are crucial in cybersecurity, with forensic analysts focusing on post-incident investigation and threat hunters emphasizing real-time detection and mitigation.
Key Responsibilities and Duties
A Forensic Analyst specializes in collecting, analyzing, and preserving digital evidence from security incidents to support investigations and legal proceedings. Threat Hunters proactively search for cyber threats and vulnerabilities within an organization's network using advanced detection techniques and behavioral analysis. Both roles are critical for comprehensive cybersecurity, with Forensic Analysts focusing on incident response and evidence documentation, while Threat Hunters emphasize threat detection and prevention.
Core Skills and Competencies
Forensic analysts excel in digital evidence collection, preservation, and detailed examination of cyber incidents, emphasizing expertise in data recovery, malware analysis, and chain of custody protocols. Threat hunters focus on proactive detection and mitigation of advanced persistent threats (APTs), requiring strong skills in behavioral analytics, threat intelligence, and real-time network monitoring. Both roles demand deep knowledge of cybersecurity frameworks, but forensic analysts prioritize post-incident investigation while threat hunters emphasize continuous threat detection and response.
Required Certifications and Education
Forensic analysts typically require certifications such as Certified Computer Examiner (CCE) or GIAC Certified Forensic Analyst (GCFA), alongside a background in computer science, information security, or digital forensics. Threat hunters often pursue certifications like GIAC Cyber Threat Intelligence (GCTI) or Certified Threat Intelligence Analyst (CTIA), combined with expertise in network security, malware analysis, and threat detection methodologies. Both roles demand continuous education in cybersecurity frameworks and hands-on experience to stay current with evolving threat landscapes.
Daily Tools and Technologies
Forensic Analysts primarily utilize tools such as EnCase, FTK, and Autopsy for disk imaging, data recovery, and detailed post-incident analysis. Threat Hunters leverage advanced tools like Splunk, ELK Stack, and CrowdStrike to proactively detect and investigate potential threats in real-time network environments. Both roles rely on endpoint detection and response (EDR) platforms and threat intelligence feeds to enhance their investigative capabilities and ensure comprehensive security monitoring.
Typical Work Environments
Forensic Analysts typically operate within law enforcement agencies, cybersecurity firms, and corporate IT departments, analyzing digital evidence from cybercrime incidents in controlled lab environments. Threat Hunters function primarily in Security Operations Centers (SOCs), managed security service providers (MSSPs), and enterprise networks, proactively searching for cyber threats in live, real-time systems. Both roles demand access to advanced forensic tools and threat intelligence platforms to support incident response and mitigation efforts.
Investigation vs Proactive Defense
Forensic analysts specialize in investigation by meticulously examining digital evidence to reconstruct cyber incidents and determine the cause and extent of breaches. Threat hunters engage in proactive defense, continuously searching network environments for hidden threats and Indicators of Compromise (IOCs) before attacks can escalate. The synergy between forensic analysis and threat hunting enhances organizational cybersecurity by combining detailed post-incident investigation with cutting-edge threat detection strategies.
Career Pathways and Advancement
Forensic Analysts specialize in investigating cybercrimes by analyzing digital evidence and reconstructing security incidents, often advancing into roles like Senior Forensic Investigator or Incident Response Manager. Threat Hunters proactively search for hidden threats and vulnerabilities within networks, with career progression paths leading to positions such as Threat Intelligence Analyst or Cyber Threat Operations Lead. Both roles require continuous skill development in cybersecurity tools and techniques, with certifications like GIAC Certified Forensic Analyst (GCFA) or Certified Threat Intelligence Analyst (CTIA) enhancing advancement opportunities.
Salary Expectations and Job Outlook
Forensic Analysts typically earn an average salary between $70,000 and $110,000 annually, driven by their expertise in investigating cybercrimes and analyzing digital evidence. Threat Hunters command salaries ranging from $80,000 to $130,000, reflecting their proactive role in identifying and mitigating advanced cyber threats. The job outlook for both roles is strong, with the cybersecurity sector expected to grow by over 31% from 2021 to 2031, fueling high demand for professionals skilled in forensic analysis and threat hunting.
Choosing the Right Role for You
Forensic analysts specialize in investigating cyber incidents by analyzing digital evidence to determine the cause and extent of security breaches, making this role ideal for those detail-oriented and methodical in approach. Threat hunters proactively seek out potential cyber threats and vulnerabilities before attacks occur, requiring strong analytical skills and up-to-date threat intelligence knowledge. Choosing the right role depends on whether you prefer reactive, evidence-driven investigation or proactive, strategic threat detection within cybersecurity operations.
Forensic Analyst vs Threat Hunter Infographic
 jobdiv.com
jobdiv.com