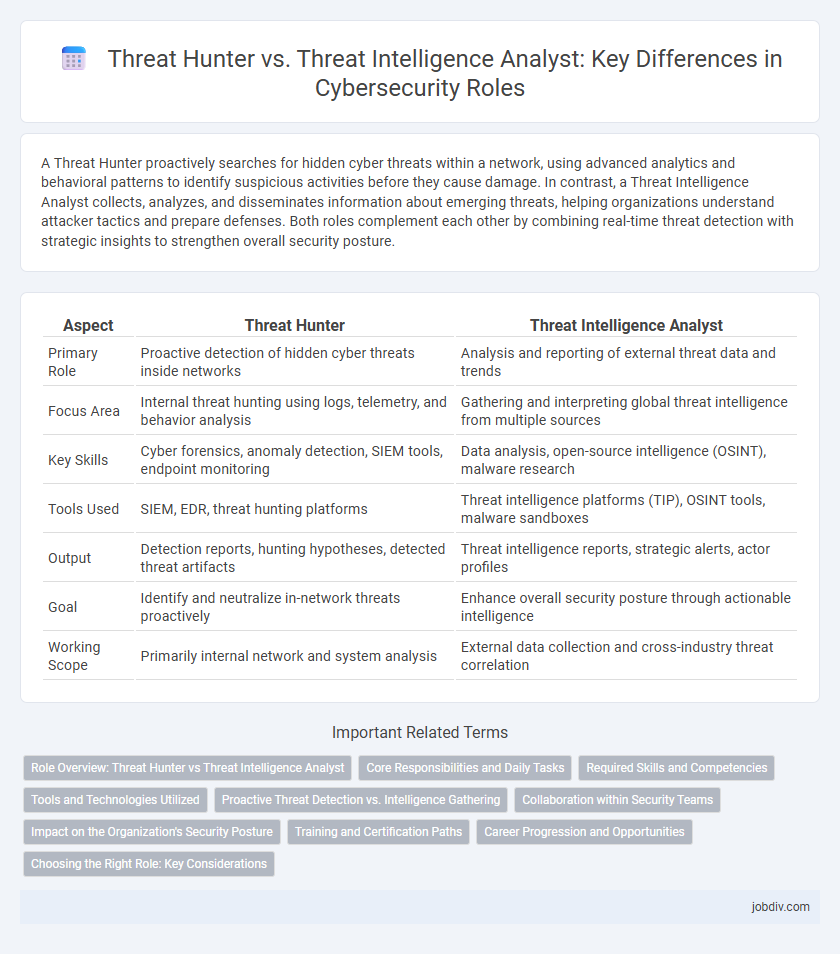
A Threat Hunter proactively searches for hidden cyber threats within a network, using advanced analytics and behavioral patterns to identify suspicious activities before they cause damage. In contrast, a Threat Intelligence Analyst collects, analyzes, and disseminates information about emerging threats, helping organizations understand attacker tactics and prepare defenses. Both roles complement each other by combining real-time threat detection with strategic insights to strengthen overall security posture.
Table of Comparison
| Aspect | Threat Hunter | Threat Intelligence Analyst |
|---|---|---|
| Primary Role | Proactive detection of hidden cyber threats inside networks | Analysis and reporting of external threat data and trends |
| Focus Area | Internal threat hunting using logs, telemetry, and behavior analysis | Gathering and interpreting global threat intelligence from multiple sources |
| Key Skills | Cyber forensics, anomaly detection, SIEM tools, endpoint monitoring | Data analysis, open-source intelligence (OSINT), malware research |
| Tools Used | SIEM, EDR, threat hunting platforms | Threat intelligence platforms (TIP), OSINT tools, malware sandboxes |
| Output | Detection reports, hunting hypotheses, detected threat artifacts | Threat intelligence reports, strategic alerts, actor profiles |
| Goal | Identify and neutralize in-network threats proactively | Enhance overall security posture through actionable intelligence |
| Working Scope | Primarily internal network and system analysis | External data collection and cross-industry threat correlation |
Role Overview: Threat Hunter vs Threat Intelligence Analyst
Threat Hunters proactively search for hidden threats within networks, employing advanced analytics and behavioral analysis to identify anomalies often missed by automated systems. Threat Intelligence Analysts gather, analyze, and interpret data on emerging cyber threats, providing actionable insights to guide defensive strategies and inform security teams. Both roles are critical in a comprehensive cybersecurity framework, focusing respectively on detection and strategic threat assessment.
Core Responsibilities and Daily Tasks
Threat Hunters actively search for unknown cyber threats within networks using advanced analytics, behavioral analysis, and threat detection tools, focusing on identifying and mitigating emerging threats before they cause damage. Threat Intelligence Analysts collect, analyze, and interpret data on cyber threats from multiple sources to provide actionable intelligence and strategic insights that inform security policies and defenses. While Threat Hunters are hands-on with real-time threat detection and incident response, Threat Intelligence Analysts emphasize research, trend analysis, and reporting to support long-term security planning.
Required Skills and Competencies
Threat Hunters require advanced skills in behavioral analytics, malware reverse engineering, and proactive threat detection methodologies to identify hidden adversaries within networks. Threat Intelligence Analysts excel in gathering, analyzing, and contextualizing cyber threat data from multiple sources, with strong competencies in data correlation, report writing, and communication to support strategic security decisions. Both roles demand expertise in cybersecurity frameworks, incident response, and continuous learning to adapt to evolving threat landscapes.
Tools and Technologies Utilized
Threat Hunters primarily leverage advanced behavioral analytics platforms, endpoint detection and response (EDR) tools, and custom threat hunting frameworks to identify anomalies within network traffic and endpoint data. Threat Intelligence Analysts utilize centralized threat intelligence platforms, open-source intelligence (OSINT) tools, and automated data aggregation systems to collect, analyze, and disseminate actionable threat information. Both roles integrate threat feeds and SIEM (Security Information and Event Management) solutions, but Threat Hunters focus on proactive detection while Analysts emphasize strategic intelligence curation.
Proactive Threat Detection vs. Intelligence Gathering
Threat Hunters excel in proactive threat detection by actively searching for indicators of compromise and anomalies within networks to identify and mitigate emerging threats before they cause damage. Threat Intelligence Analysts focus on intelligence gathering by collecting, analyzing, and disseminating data from various sources to understand threat actor tactics, techniques, and procedures (TTPs). Combining the proactive approach of Threat Hunters with the strategic insights from Threat Intelligence Analysts enhances an organization's overall security posture and reduces response times to cyber threats.
Collaboration within Security Teams
Threat Hunters and Threat Intelligence Analysts enhance security team collaboration by sharing real-time data and insights, enabling proactive threat detection and response. Threat Hunters provide on-the-ground investigation results that refine threat intelligence, while Analysts contextualize and prioritize these findings for strategic defense initiatives. This synergy accelerates incident resolution and strengthens overall organizational cybersecurity posture.
Impact on the Organization's Security Posture
Threat Hunters proactively detect and neutralize hidden threats within an organization's network, significantly reducing the risk of advanced persistent threats and minimizing potential breaches. Threat Intelligence Analysts gather and analyze external threat data, enabling informed decision-making and strategic defense planning to anticipate and counter evolving cyber threats. Together, these roles enhance the organization's security posture by combining proactive threat detection with comprehensive intelligence-driven insights.
Training and Certification Paths
Threat Hunters typically pursue certifications like GIAC Cyber Threat Hunting (GCTH) and Certified Threat Hunting Professional (CTHP), emphasizing hands-on skills in proactive threat detection and behavioral analysis. Threat Intelligence Analysts often obtain credentials such as the Certified Threat Intelligence Analyst (CTIA) and GIAC Cyber Threat Intelligence (GCTI), focusing on strategic analysis, data correlation, and intelligence reporting. Both roles benefit from continuous training in malware analysis, network forensics, and emerging threat landscapes to stay ahead of evolving cyber threats.
Career Progression and Opportunities
Threat Hunters advance by developing expertise in proactive incident detection, mastering behavioral analysis, and utilizing advanced threat-hunting tools to uncover hidden cyber threats. Threat Intelligence Analysts progress through roles involving strategic analysis of global cyber threat trends, integrating intelligence from diverse sources, and advising on risk mitigation to inform organizational defense strategies. Both career paths offer opportunities in cybersecurity leadership, but Threat Intelligence Analysts often move towards policy and strategy development, while Threat Hunters generally advance into hands-on incident response and threat mitigation roles.
Choosing the Right Role: Key Considerations
Choosing between a Threat Hunter and a Threat Intelligence Analyst depends on organizational needs for proactive detection versus strategic analysis. Threat Hunters specialize in identifying hidden threats within networks through advanced forensic techniques and behavioral analytics, ideal for real-time incident response. Threat Intelligence Analysts focus on gathering, analyzing, and interpreting external threat data to inform security posture and anticipate emerging risks, crucial for long-term risk management and informed decision-making.
Threat Hunter vs Threat Intelligence Analyst Infographic
 jobdiv.com
jobdiv.com