Red Team Operators simulate cyberattacks, identifying vulnerabilities through offensive tactics to strengthen organizational defenses. Blue Team Operators focus on detecting, responding to, and mitigating security breaches, maintaining continuous protection of systems. Both roles are crucial in developing a comprehensive security strategy that proactively addresses threats and minimizes risks.
Table of Comparison
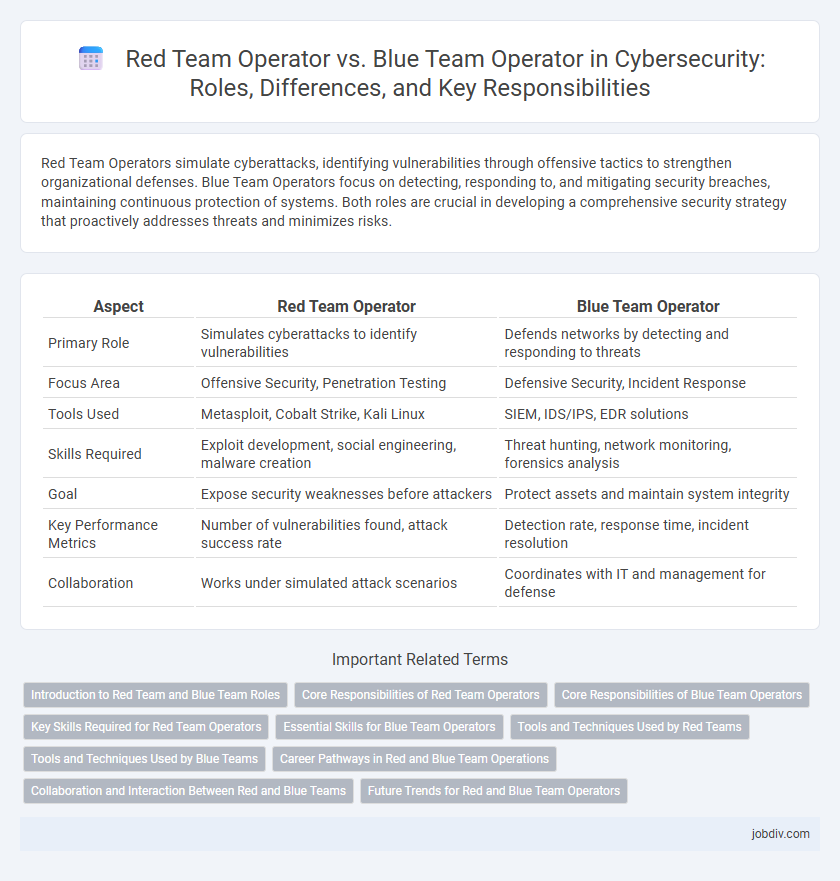
| Aspect | Red Team Operator | Blue Team Operator |
|---|---|---|
| Primary Role | Simulates cyberattacks to identify vulnerabilities | Defends networks by detecting and responding to threats |
| Focus Area | Offensive Security, Penetration Testing | Defensive Security, Incident Response |
| Tools Used | Metasploit, Cobalt Strike, Kali Linux | SIEM, IDS/IPS, EDR solutions |
| Skills Required | Exploit development, social engineering, malware creation | Threat hunting, network monitoring, forensics analysis |
| Goal | Expose security weaknesses before attackers | Protect assets and maintain system integrity |
| Key Performance Metrics | Number of vulnerabilities found, attack success rate | Detection rate, response time, incident resolution |
| Collaboration | Works under simulated attack scenarios | Coordinates with IT and management for defense |
Introduction to Red Team and Blue Team Roles
Red Team Operators simulate realistic cyberattacks to identify vulnerabilities and test an organization's security defenses, employing tactics such as penetration testing, social engineering, and vulnerability exploitation. Blue Team Operators focus on defending IT infrastructures by monitoring systems, analyzing threats, and responding to incidents in real-time to prevent or mitigate attacks. Both roles are essential in cybersecurity strategies, enhancing organizational resilience through proactive offense and robust defense mechanisms.
Core Responsibilities of Red Team Operators
Red Team Operators specialize in simulating real-world cyber attacks to identify vulnerabilities within an organization's security defenses. Their core responsibilities include executing penetration tests, developing sophisticated attack strategies, and exploiting system weaknesses to assess risk exposure. They provide detailed reports with actionable insights that help strengthen overall security posture against potential breaches.
Core Responsibilities of Blue Team Operators
Blue Team Operators are responsible for monitoring, detecting, and responding to cybersecurity threats within an organization's network. They utilize tools such as Security Information and Event Management (SIEM) systems, intrusion detection systems (IDS), and endpoint detection and response (EDR) to protect critical assets. Their core duties include incident response, vulnerability management, and continuous security assessment to maintain a strong defense posture.
Key Skills Required for Red Team Operators
Red Team Operators require advanced penetration testing skills, in-depth knowledge of adversary tactics, techniques, and procedures (TTPs), and proficiency in social engineering methods. Expertise in network exploitation, vulnerability assessment, and stealthy persistence techniques is essential for simulating real-world attacks. Strong analytical abilities and experience with various offensive security tools such as Metasploit, Cobalt Strike, and custom payload development significantly enhance the effectiveness of Red Team engagements.
Essential Skills for Blue Team Operators
Blue Team Operators require expertise in incident detection, threat analysis, and system hardening to effectively defend organizational networks. Proficiency in security information and event management (SIEM) tools, intrusion detection systems (IDS), and malware analysis enables rapid identification and remediation of potential breaches. Strong knowledge of network protocols, vulnerability assessment, and security frameworks is critical for maintaining resilient defenses against advanced persistent threats.
Tools and Techniques Used by Red Teams
Red Team Operators utilize advanced penetration testing tools such as Cobalt Strike, Metasploit, and custom malware to simulate realistic cyberattacks, exploiting vulnerabilities across networks, applications, and endpoints. They employ social engineering techniques, phishing campaigns, and lateral movement tactics to mimic adversaries and assess an organization's detection and response capabilities. These operators leverage stealthy command and control (C2) infrastructures and advanced evasion methods to bypass defenses and provide comprehensive security assessments.
Tools and Techniques Used by Blue Teams
Blue Team operators primarily utilize security information and event management (SIEM) tools like Splunk and IBM QRadar to monitor, detect, and analyze threats in real time. Endpoint detection and response (EDR) solutions such as CrowdStrike Falcon and Carbon Black enable continuous threat detection and rapid incident response across devices. Network traffic analysis tools including Zeek and Wireshark help Blue Teams identify suspicious activities and protect organizational assets through proactive threat hunting and vulnerability management.
Career Pathways in Red and Blue Team Operations
Red Team Operators specialize in offensive security tactics, including penetration testing and social engineering, to simulate cyberattacks and identify vulnerabilities, paving the way to roles like Ethical Hacker or Penetration Tester. Blue Team Operators focus on defensive measures such as threat detection, incident response, and security monitoring, often advancing to positions like Security Analyst or Incident Responder. Both career pathways require continuous skill development in emerging technologies and cybersecurity frameworks to effectively safeguard organizational assets.
Collaboration and Interaction Between Red and Blue Teams
Red Team Operators simulate cyberattacks to identify vulnerabilities, while Blue Team Operators defend networks by detecting and responding to threats. Effective collaboration between Red and Blue Teams enhances organizational security by enabling real-time feedback and adaptive defense strategies. Shared insights and coordinated exercises foster resilience against evolving cyber threats through continuous improvement in tactics and technologies.
Future Trends for Red and Blue Team Operators
Red Team Operators are increasingly leveraging artificial intelligence and machine learning to simulate advanced persistent threats and automate complex attack scenarios, enhancing their ability to identify vulnerabilities in real-time. Blue Team Operators are adopting advanced threat detection platforms powered by behavioral analytics and zero-trust architectures to proactively defend against sophisticated cyberattacks. Emerging trends include the integration of automated response systems and Continuous Security Validation (CSV) to bridge the gap between offensive and defensive cybersecurity strategies.
Red Team Operator vs Blue Team Operator Infographic
 jobdiv.com
jobdiv.com