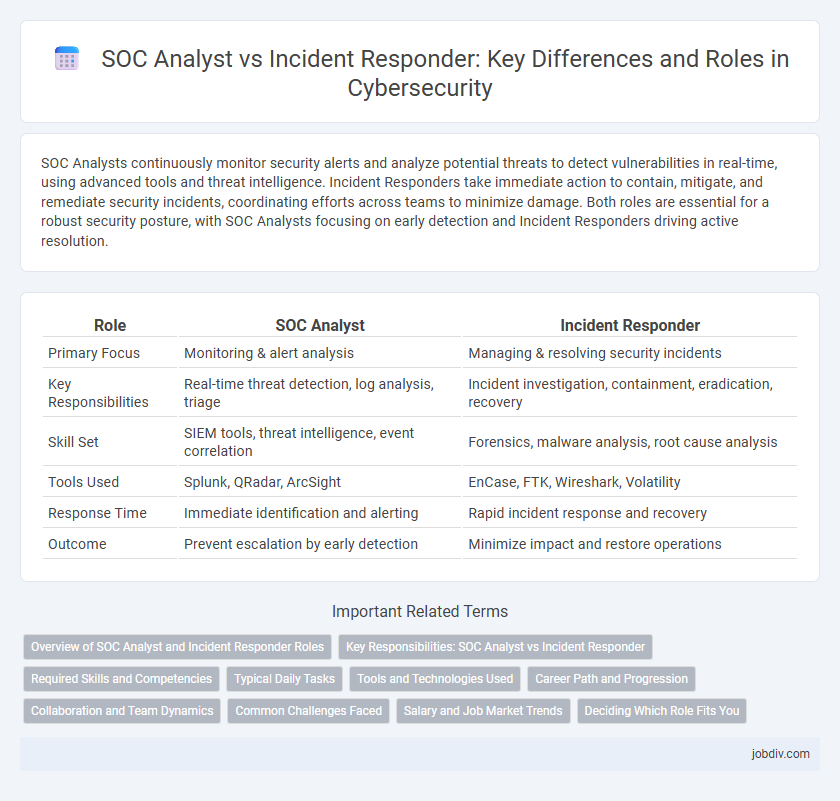
SOC Analysts continuously monitor security alerts and analyze potential threats to detect vulnerabilities in real-time, using advanced tools and threat intelligence. Incident Responders take immediate action to contain, mitigate, and remediate security incidents, coordinating efforts across teams to minimize damage. Both roles are essential for a robust security posture, with SOC Analysts focusing on early detection and Incident Responders driving active resolution.
Table of Comparison
| Role | SOC Analyst | Incident Responder |
|---|---|---|
| Primary Focus | Monitoring & alert analysis | Managing & resolving security incidents |
| Key Responsibilities | Real-time threat detection, log analysis, triage | Incident investigation, containment, eradication, recovery |
| Skill Set | SIEM tools, threat intelligence, event correlation | Forensics, malware analysis, root cause analysis |
| Tools Used | Splunk, QRadar, ArcSight | EnCase, FTK, Wireshark, Volatility |
| Response Time | Immediate identification and alerting | Rapid incident response and recovery |
| Outcome | Prevent escalation by early detection | Minimize impact and restore operations |
Overview of SOC Analyst and Incident Responder Roles
SOC Analysts monitor security systems to detect and analyze threats, utilizing tools like SIEM platforms to identify vulnerabilities and potential breaches. Incident Responders take immediate action during security incidents, conducting investigations, containing threats, and coordinating recovery efforts to minimize damage. Both roles are critical in a Security Operations Center, with SOC Analysts focusing on proactive threat detection and Incident Responders addressing active security events.
Key Responsibilities: SOC Analyst vs Incident Responder
SOC Analysts focus on continuous monitoring of security alerts, identifying potential threats, and conducting initial triage to categorize incidents. Incident Responders handle the in-depth investigation, containment, eradication, and recovery processes during security breaches. Both roles collaborate closely to ensure timely detection, response, and mitigation of cybersecurity incidents.
Required Skills and Competencies
SOC Analysts require strong skills in security monitoring, threat detection, and log analysis, with expertise in SIEM tools, network protocols, and incident classification. Incident Responders need advanced competencies in forensic investigation, malware analysis, and containment strategies, alongside proficiency in scripting and communication for coordinating response efforts. Both roles demand deep understanding of cybersecurity frameworks, rapid decision-making under pressure, and continuous knowledge of evolving threats.
Typical Daily Tasks
SOC Analysts monitor security alerts, analyze logs, and escalate potential threats through centralized SIEM platforms, ensuring continuous network defense. Incident Responders investigate confirmed breaches, perform root cause analysis, and coordinate containment efforts to mitigate ongoing cyber incidents. Both roles rely heavily on threat intelligence, forensic tools, and incident documentation to maintain organizational security posture.
Tools and Technologies Used
SOC Analysts primarily utilize Security Information and Event Management (SIEM) platforms like Splunk and IBM QRadar to monitor real-time alerts and analyze security events, while leveraging endpoint detection and response (EDR) tools such as CrowdStrike and Carbon Black for threat detection. Incident Responders employ advanced forensics software such as EnCase and FTK alongside network traffic analyzers like Wireshark to investigate and contain security breaches effectively. Both roles integrate automation tools like SOAR (Security Orchestration, Automation, and Response) to enhance workflow efficiency and incident management.
Career Path and Progression
SOC Analysts typically start with monitoring and analyzing security events, gaining expertise in threat detection and vulnerability assessment. Incident Responders leverage this foundational experience to develop advanced skills in incident investigation, containment, and remediation, often progressing toward senior security roles or specialized incident response teams. Career advancement frequently involves certifications like CISSP or GIAC certifications, enhancing opportunities for leadership positions in cybersecurity operations or incident management.
Collaboration and Team Dynamics
SOC Analysts and Incident Responders collaborate closely to enhance organizational security by combining real-time threat monitoring with rapid incident handling. Effective team dynamics hinge on clear communication, where SOC Analysts provide detailed threat intelligence that enables Incident Responders to execute timely containment and remediation strategies. This synergy ensures a proactive defense posture and minimizes the impact of security breaches through coordinated efforts.
Common Challenges Faced
SOC Analysts and Incident Responders both encounter challenges such as managing alert fatigue from high volumes of false positives, which hampers effective threat detection and response. Limited visibility into complex attack vectors complicates precise incident identification, requiring advanced threat intelligence and correlation tools. Coordination gaps between teams and insufficient real-time data sharing often delay containment and remediation efforts, impacting overall security posture.
Salary and Job Market Trends
SOC Analysts typically earn between $65,000 and $95,000 annually, reflecting steady demand in cybersecurity operations centers. Incident Responders command higher salaries, often ranging from $85,000 to $120,000, driven by specialized skills in threat mitigation and breach management. Job market trends indicate a growing need for both roles, with Incident Responders experiencing faster salary growth due to the increasing frequency of sophisticated cyberattacks.
Deciding Which Role Fits You
Choosing between a SOC Analyst and an Incident Responder depends on your preference for proactive monitoring versus reactive problem-solving in cybersecurity. SOC Analysts specialize in continuous threat detection and analysis through real-time security alerts, while Incident Responders focus on investigating, mitigating, and recovering from security incidents. Assess your skills in pattern recognition, response urgency, and teamwork to determine which role aligns best with your career goals.
SOC Analyst vs Incident Responder Infographic
 jobdiv.com
jobdiv.com