Red Teamers simulate realistic cyberattacks to identify vulnerabilities and test an organization's defenses, pushing systems to their limits through ethical hacking techniques. Blue Teamers focus on defending networks by monitoring, detecting, and responding to threats in real-time, ensuring robust incident response and reinforcing security protocols. Collaboration between Red and Blue Teams enhances an organization's overall security posture through continuous assessment and improvement.
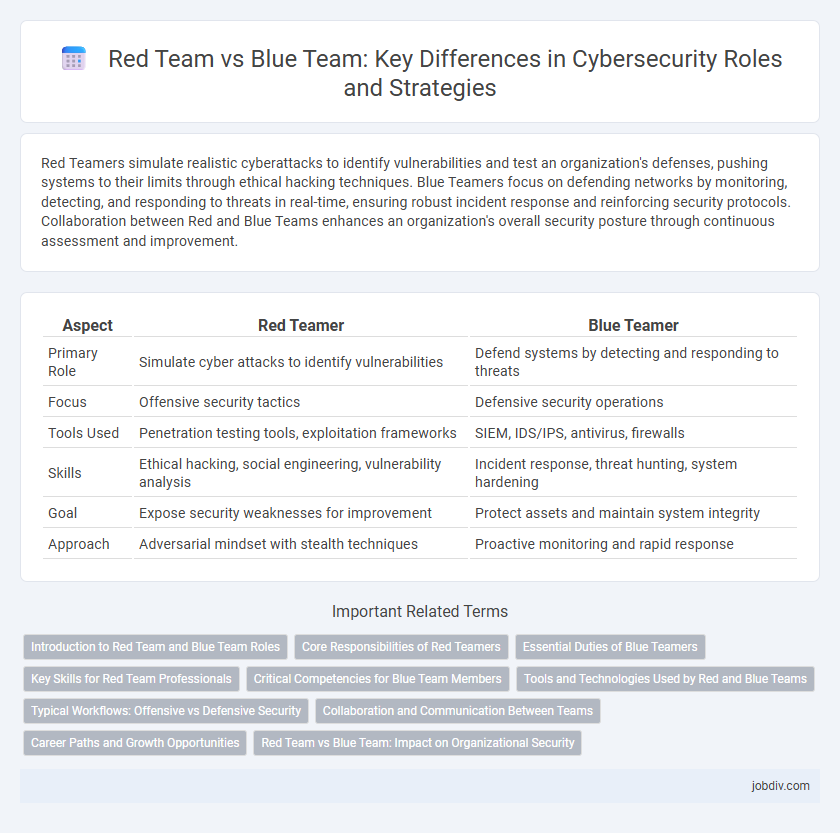
Table of Comparison
| Aspect | Red Teamer | Blue Teamer |
|---|---|---|
| Primary Role | Simulate cyber attacks to identify vulnerabilities | Defend systems by detecting and responding to threats |
| Focus | Offensive security tactics | Defensive security operations |
| Tools Used | Penetration testing tools, exploitation frameworks | SIEM, IDS/IPS, antivirus, firewalls |
| Skills | Ethical hacking, social engineering, vulnerability analysis | Incident response, threat hunting, system hardening |
| Goal | Expose security weaknesses for improvement | Protect assets and maintain system integrity |
| Approach | Adversarial mindset with stealth techniques | Proactive monitoring and rapid response |
Introduction to Red Team and Blue Team Roles
Red Team members simulate real-world cyberattacks to identify vulnerabilities, using offensive tactics such as penetration testing, social engineering, and exploitation of weaknesses. Blue Team professionals focus on defending organizational assets by monitoring networks, analyzing threats, and implementing incident response strategies to mitigate risks. Together, these teams enhance cybersecurity resilience through adversarial simulation and defense preparedness.
Core Responsibilities of Red Teamers
Red Teamers specialize in simulating real-world cyberattacks to identify vulnerabilities in an organization's security infrastructure. Their core responsibilities include penetration testing, social engineering, and exploiting system weaknesses to assess the effectiveness of defensive measures. By mimicking advanced persistent threats, Red Teamers provide actionable insights that help strengthen overall cybersecurity resilience.
Essential Duties of Blue Teamers
Blue Teamers are responsible for continuously monitoring network traffic, analyzing potential threats, and implementing defensive measures to safeguard organizational assets. They conduct vulnerability assessments, maintain intrusion detection systems, and respond swiftly to security incidents to minimize damage. Their role includes developing security policies, performing regular system audits, and collaborating with other teams to enhance overall cybersecurity posture.
Key Skills for Red Team Professionals
Red Team professionals excel in penetration testing, vulnerability exploitation, and social engineering to simulate real-world cyberattacks. Expertise in advanced threat modeling, ethical hacking tools like Metasploit, and covert network intrusion techniques enables them to identify and exploit security weaknesses effectively. Mastery of scripting languages such as Python and deep knowledge of operating systems and network protocols are essential for crafting sophisticated attack scenarios.
Critical Competencies for Blue Team Members
Blue Team members must possess critical competencies in network defense, incident detection, and real-time threat analysis to effectively protect organizational assets. Proficiency in security information and event management (SIEM) tools, forensics, and vulnerability assessment enables rapid identification and mitigation of attacks. Mastery of intrusion detection systems (IDS), firewall configuration, and secure system architecture fortifies defenses against Red Team adversaries.
Tools and Technologies Used by Red and Blue Teams
Red Teams primarily utilize penetration testing tools like Metasploit, Cobalt Strike, and custom malware to simulate cyber attacks and identify vulnerabilities. Blue Teams leverage security information and event management (SIEM) systems such as Splunk, endpoint detection and response (EDR) tools like CrowdStrike, and network monitoring solutions to detect, analyze, and respond to threats in real time. Both teams employ threat intelligence platforms and utilize automation tools to enhance their offensive and defensive capabilities within cybersecurity operations.
Typical Workflows: Offensive vs Defensive Security
Red Teamers simulate real-world cyberattacks by identifying vulnerabilities and exploiting weaknesses in target systems to test organizational defenses. Blue Teamers focus on monitoring, detecting, and responding to these threats through continuous network analysis, incident response, and system hardening. Collaboration between Red and Blue Teams enhances an organization's overall security posture by ensuring vulnerabilities are effectively identified and mitigated.
Collaboration and Communication Between Teams
Effective collaboration and communication between Red Teamers and Blue Teamers maximize the security posture by enabling rapid identification and mitigation of vulnerabilities. Regular information sharing, joint briefings, and synchronized attack simulations ensure both teams understand evolving threat tactics and defense mechanisms. Integrating feedback loops fosters continuous improvement, transforming adversarial exercises into collaborative learning opportunities that strengthen organizational resilience.
Career Paths and Growth Opportunities
Red Teamers specialize in offensive security, honing skills in ethical hacking, penetration testing, and vulnerability assessment, making their career path ideal for roles like ethical hackers, security consultants, and vulnerability analysts. Blue Teamers focus on defensive security measures, incident response, and threat detection, leading to growth opportunities as security analysts, incident responders, and security operations center (SOC) managers. Both career paths offer strong advancement potential, but Red Team roles tend to emphasize creativity and exploitation techniques, while Blue Team roles prioritize risk management and system hardening.
Red Team vs Blue Team: Impact on Organizational Security
Red Team versus Blue Team exercises significantly enhance organizational security by identifying vulnerabilities and testing defense mechanisms under realistic attack scenarios. The Red Team simulates adversarial tactics to expose weaknesses, while the Blue Team focuses on detecting, responding to, and mitigating threats in real time. This adversarial collaboration drives continuous improvement in security posture, incident response capabilities, and overall resilience against cyber threats.
Red Teamer vs Blue Teamer Infographic
 jobdiv.com
jobdiv.com