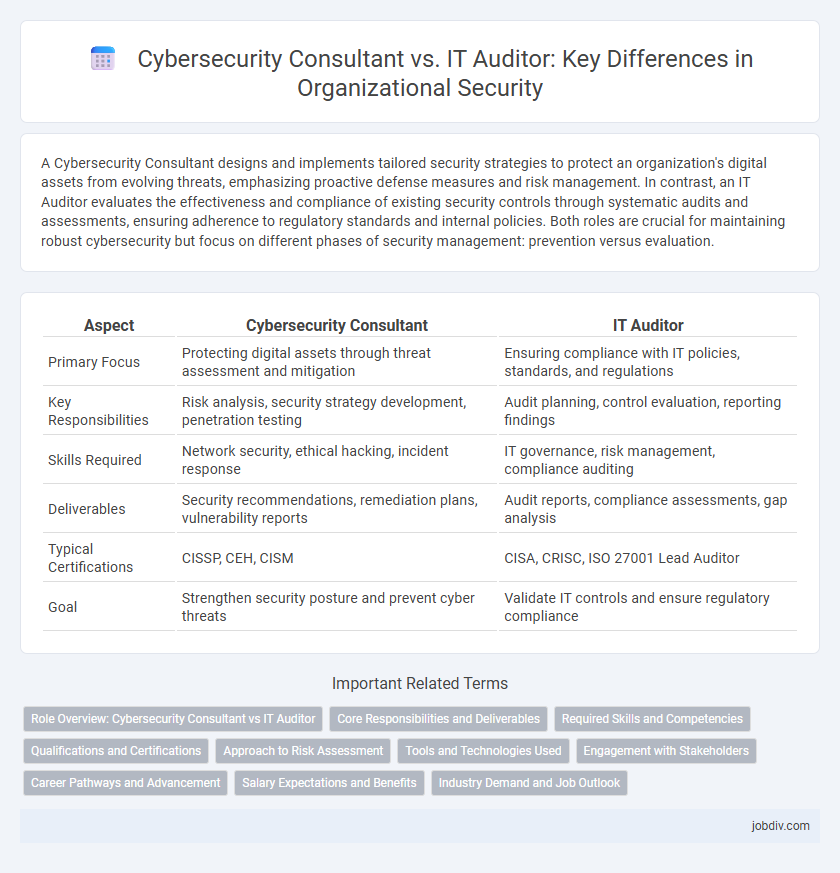
A Cybersecurity Consultant designs and implements tailored security strategies to protect an organization's digital assets from evolving threats, emphasizing proactive defense measures and risk management. In contrast, an IT Auditor evaluates the effectiveness and compliance of existing security controls through systematic audits and assessments, ensuring adherence to regulatory standards and internal policies. Both roles are crucial for maintaining robust cybersecurity but focus on different phases of security management: prevention versus evaluation.
Table of Comparison
| Aspect | Cybersecurity Consultant | IT Auditor |
|---|---|---|
| Primary Focus | Protecting digital assets through threat assessment and mitigation | Ensuring compliance with IT policies, standards, and regulations |
| Key Responsibilities | Risk analysis, security strategy development, penetration testing | Audit planning, control evaluation, reporting findings |
| Skills Required | Network security, ethical hacking, incident response | IT governance, risk management, compliance auditing |
| Deliverables | Security recommendations, remediation plans, vulnerability reports | Audit reports, compliance assessments, gap analysis |
| Typical Certifications | CISSP, CEH, CISM | CISA, CRISC, ISO 27001 Lead Auditor |
| Goal | Strengthen security posture and prevent cyber threats | Validate IT controls and ensure regulatory compliance |
Role Overview: Cybersecurity Consultant vs IT Auditor
A Cybersecurity Consultant specializes in identifying vulnerabilities, designing robust security architectures, and implementing proactive measures to protect information systems from cyber threats. An IT Auditor evaluates an organization's IT infrastructure, policies, and controls to ensure compliance with regulatory standards and to assess the effectiveness of risk management strategies. Both roles play critical parts in maintaining cybersecurity, with the consultant focusing on defense and optimization, while the auditor concentrates on validation and regulatory adherence.
Core Responsibilities and Deliverables
Cybersecurity consultants specialize in identifying vulnerabilities, designing security architectures, and implementing protective measures to safeguard organizational digital assets. IT auditors focus on evaluating the effectiveness of IT controls, ensuring compliance with regulatory standards, and delivering audit reports that highlight risks and recommend remediation. Both roles contribute to robust security postures, with consultants driving proactive defense strategies and auditors providing independent assurance through systematic assessments.
Required Skills and Competencies
Cybersecurity consultants require advanced expertise in risk assessment, threat modeling, and security architecture, alongside proficiency in penetration testing and incident response. IT auditors need strong knowledge of compliance frameworks like ISO 27001, SOX, and COBIT, combined with skills in internal controls evaluation, audit planning, and IT governance analysis. Both roles demand analytical thinking, attention to detail, and effective communication skills to interpret complex technical data and advise stakeholders.
Qualifications and Certifications
Cybersecurity Consultants typically hold certifications such as Certified Information Systems Security Professional (CISSP) and Certified Ethical Hacker (CEH) to demonstrate expertise in threat identification and mitigation strategies. IT Auditors often pursue Certified Information Systems Auditor (CISA) credentials to validate their proficiency in evaluating IT controls and compliance frameworks. Both roles require strong foundational knowledge in information security, but Cybersecurity Consultants emphasize offensive and defensive tactics while IT Auditors focus on risk assessment and regulatory adherence.
Approach to Risk Assessment
Cybersecurity consultants adopt a proactive risk assessment approach by identifying vulnerabilities and recommending tailored security measures to prevent breaches. IT auditors focus on evaluating existing controls and compliance with policies to ensure risk management effectiveness. While consultants emphasize continuous improvement through risk identification, auditors prioritize verification and validation of implemented safeguards.
Tools and Technologies Used
Cybersecurity consultants leverage advanced tools like vulnerability scanners (e.g., Nessus), penetration testing frameworks (e.g., Metasploit), and Security Information and Event Management (SIEM) systems to proactively identify and mitigate threats. IT auditors utilize auditing software such as ACL, IDEA, and GRC platforms like RSA Archer to evaluate compliance, operational controls, and risk management processes within IT environments. Both roles require proficiency with network monitoring tools, but consultants emphasize offensive security technologies, while auditors focus on ensuring regulatory adherence and control effectiveness.
Engagement with Stakeholders
Cybersecurity Consultants collaborate closely with stakeholders to identify vulnerabilities and design tailored security strategies that align with business objectives, ensuring proactive risk management. IT Auditors engage stakeholders primarily to evaluate compliance with internal controls and regulatory standards, providing objective assessments and recommendations for improving IT governance. Both roles require effective communication skills to translate technical findings into actionable insights for diverse business audiences.
Career Pathways and Advancement
Cybersecurity consultants leverage specialized expertise in threat detection and risk mitigation, often progressing towards roles like Chief Information Security Officer (CISO) or Security Architect. IT auditors focus on evaluating compliance and internal controls, paving the way to senior audit manager or IT governance roles. Both career paths demand continuous certification, with cybersecurity consultants favoring CISSP or CEH, while IT auditors pursue CISA or CRISC credentials for advancement.
Salary Expectations and Benefits
Cybersecurity consultants typically command higher salaries than IT auditors due to their specialized skills in threat analysis and proactive defense strategies, with average annual earnings ranging from $90,000 to $130,000. IT auditors earn between $70,000 and $110,000, reflecting their focus on compliance, risk assessment, and internal controls. Benefits for cybersecurity consultants often include bonuses tied to incident prevention success, while IT auditors may receive perks related to professional certifications and continuous education support.
Industry Demand and Job Outlook
Cybersecurity consultants are experiencing rapid industry demand due to increasing cyber threats and the need for advanced defense strategies across multiple sectors, with projected job growth exceeding 30% over the next decade. IT auditors maintain steady demand, primarily driven by regulatory compliance and risk management requirements, with employment growth expected around 10-15%. Organizations increasingly prioritize proactive security measures, heightening the value of consultants while auditors remain essential for ensuring ongoing adherence to security standards.
Cybersecurity Consultant vs IT Auditor Infographic
 jobdiv.com
jobdiv.com