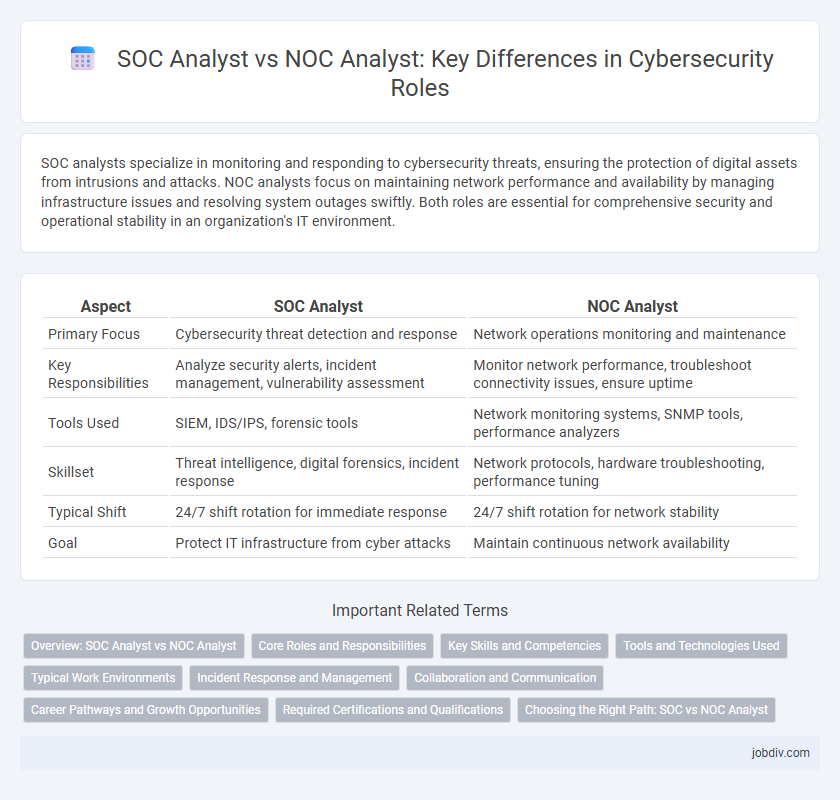
SOC analysts specialize in monitoring and responding to cybersecurity threats, ensuring the protection of digital assets from intrusions and attacks. NOC analysts focus on maintaining network performance and availability by managing infrastructure issues and resolving system outages swiftly. Both roles are essential for comprehensive security and operational stability in an organization's IT environment.
Table of Comparison
| Aspect | SOC Analyst | NOC Analyst |
|---|---|---|
| Primary Focus | Cybersecurity threat detection and response | Network operations monitoring and maintenance |
| Key Responsibilities | Analyze security alerts, incident management, vulnerability assessment | Monitor network performance, troubleshoot connectivity issues, ensure uptime |
| Tools Used | SIEM, IDS/IPS, forensic tools | Network monitoring systems, SNMP tools, performance analyzers |
| Skillset | Threat intelligence, digital forensics, incident response | Network protocols, hardware troubleshooting, performance tuning |
| Typical Shift | 24/7 shift rotation for immediate response | 24/7 shift rotation for network stability |
| Goal | Protect IT infrastructure from cyber attacks | Maintain continuous network availability |
Overview: SOC Analyst vs NOC Analyst
SOC Analysts specialize in monitoring, detecting, and responding to cybersecurity threats within an organization, employing tools like SIEM and intrusion detection systems to safeguard digital assets. NOC Analysts focus on ensuring network performance and uptime, managing and troubleshooting infrastructure issues to maintain connectivity and service availability. Both roles are critical, with SOC Analysts prioritizing security incident response while NOC Analysts emphasize network health and reliability.
Core Roles and Responsibilities
SOC Analysts specialize in monitoring, detecting, and responding to cybersecurity threats through continuous analysis of security alerts and incident investigations. NOC Analysts focus on network performance, ensuring uptime and troubleshooting issues related to hardware, software, and connectivity to maintain optimal network operations. SOC Analysts prioritize threat intelligence and incident response, while NOC Analysts emphasize network stability and availability, making both roles critical but distinct in cybersecurity infrastructure management.
Key Skills and Competencies
SOC Analysts specialize in threat detection, incident response, and cybersecurity tools such as SIEM platforms, requiring expertise in malware analysis, intrusion detection, and vulnerability assessment. NOC Analysts focus on network performance, monitoring infrastructure health, and troubleshooting connectivity issues, demanding skills in network protocols, hardware management, and real-time system monitoring. Both roles require strong analytical thinking and communication skills, but SOC Analysts prioritize cybersecurity defense capabilities while NOC Analysts emphasize network stability and uptime.
Tools and Technologies Used
SOC Analysts primarily utilize Security Information and Event Management (SIEM) platforms such as Splunk, IBM QRadar, and ArcSight to detect and respond to cyber threats in real-time. NOC Analysts focus on network monitoring tools like SolarWinds, Nagios, and Cisco Prime to ensure optimal network performance and availability. Both roles leverage automated alerting systems, but SOC prioritizes threat intelligence feeds and forensic tools, while NOC emphasizes bandwidth analyzers and fault management software.
Typical Work Environments
SOC Analysts primarily operate within Security Operations Centers, utilizing advanced threat detection tools and security information and event management (SIEM) systems to monitor and respond to cyber threats in real-time. NOC Analysts work in Network Operations Centers, focusing on maintaining network uptime and performance by troubleshooting connectivity issues and managing network infrastructure. Both roles require collaboration with IT teams, but SOC Analysts emphasize cybersecurity incident response while NOC Analysts prioritize network availability and stability.
Incident Response and Management
SOC Analysts specialize in incident response by monitoring security alerts, analyzing threats, and coordinating containment and remediation efforts to mitigate cyberattacks. NOC Analysts focus on network performance and availability, addressing infrastructure issues to prevent outages but are less involved in direct cyber incident management. Effective incident response relies on the SOC team's expertise in threat detection and management, complementing the NOC's role in maintaining network stability.
Collaboration and Communication
SOC Analysts prioritize collaboration with incident response teams to quickly identify and mitigate cybersecurity threats, employing precise communication to detail threat intelligence and vulnerabilities. NOC Analysts focus on network performance and uptime, coordinating with IT teams to address infrastructure issues and maintain operational continuity through clear, timely status updates. Effective communication and collaboration between SOC and NOC Analysts ensure comprehensive security monitoring and rapid resolution of both cyber threats and network disruptions.
Career Pathways and Growth Opportunities
SOC Analysts specialize in cybersecurity incident detection and response, offering career pathways into roles such as Threat Hunter, Incident Responder, or Cybersecurity Manager. NOC Analysts focus on network infrastructure monitoring and troubleshooting, with growth opportunities leading toward Network Engineer, Systems Administrator, or IT Operations Manager. Both roles provide foundational experience for advanced certifications like CISSP or CCNP, impacting long-term career advancement in IT and security domains.
Required Certifications and Qualifications
SOC Analysts typically require certifications such as Certified Information Systems Security Professional (CISSP), Certified Information Security Manager (CISM), and CompTIA Security+ to demonstrate expertise in threat detection and incident response. NOC Analysts often hold certifications like Cisco Certified Network Associate (CCNA), CompTIA Network+, and Juniper Networks Certified Associate (JNCIA) that emphasize network infrastructure and performance monitoring. Both roles benefit from strong foundational knowledge in IT, but SOC Analysts prioritize security skills while NOC Analysts focus on network operations proficiency.
Choosing the Right Path: SOC vs NOC Analyst
SOC Analysts specialize in cybersecurity threat detection, incident response, and vulnerability management, focusing on identifying and mitigating cyber attacks. NOC Analysts primarily monitor network performance, maintain infrastructure stability, and troubleshoot connectivity issues to ensure operational continuity. Choosing between SOC and NOC roles depends on whether one prefers proactive security defense or managing network health and uptime.
SOC Analyst vs NOC Analyst Infographic
 jobdiv.com
jobdiv.com