An Information Security Manager oversees the development and implementation of policies and procedures to protect an organization's data integrity and confidentiality, ensuring compliance with legal and regulatory requirements. A Cybersecurity Manager focuses more on protecting computer systems and networks from cyber threats through proactive threat detection, incident response, and vulnerability management. Both roles are essential for safeguarding digital assets, but the Information Security Manager emphasizes strategic risk management, while the Cybersecurity Manager prioritizes technical defense mechanisms.
Table of Comparison
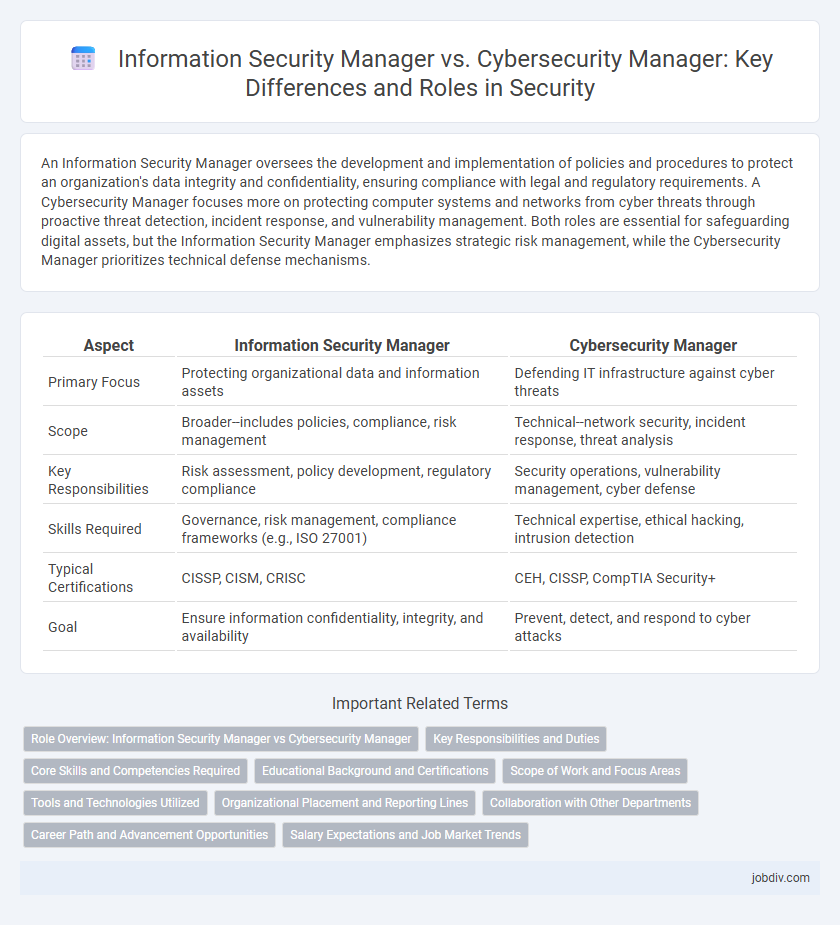
| Aspect | Information Security Manager | Cybersecurity Manager |
|---|---|---|
| Primary Focus | Protecting organizational data and information assets | Defending IT infrastructure against cyber threats |
| Scope | Broader--includes policies, compliance, risk management | Technical--network security, incident response, threat analysis |
| Key Responsibilities | Risk assessment, policy development, regulatory compliance | Security operations, vulnerability management, cyber defense |
| Skills Required | Governance, risk management, compliance frameworks (e.g., ISO 27001) | Technical expertise, ethical hacking, intrusion detection |
| Typical Certifications | CISSP, CISM, CRISC | CEH, CISSP, CompTIA Security+ |
| Goal | Ensure information confidentiality, integrity, and availability | Prevent, detect, and respond to cyber attacks |
Role Overview: Information Security Manager vs Cybersecurity Manager
Information Security Managers oversee the development and implementation of comprehensive policies that protect an organization's information assets from unauthorized access and breaches. Cybersecurity Managers focus primarily on defending IT infrastructure against cyber threats through technical controls, incident response, and threat intelligence management. Both roles require strategic planning and risk assessment but differ in scope, with Information Security Managers taking a broader approach to data governance while Cybersecurity Managers concentrate on technical defense mechanisms.
Key Responsibilities and Duties
An Information Security Manager oversees the development and implementation of security policies, risk management, and compliance with regulatory standards to protect organizational data assets. A Cybersecurity Manager focuses specifically on defending against cyber threats by managing security operations, incident response, and vulnerability assessments. Both roles require strong leadership skills, but the Information Security Manager has a broader scope encompassing governance, while the Cybersecurity Manager specializes in technical threat mitigation.
Core Skills and Competencies Required
An Information Security Manager requires expertise in risk management, regulatory compliance, and policy development to protect organizational data and ensure governance frameworks are effectively implemented. A Cybersecurity Manager demands strong technical skills in threat analysis, incident response, network security protocols, and vulnerability assessment to safeguard against active cyber threats. Both roles require leadership, strategic planning, and communication skills, but the Information Security Manager focuses more on aligning security initiatives with business objectives, while the Cybersecurity Manager emphasizes proactive defense mechanisms and technical threat mitigation.
Educational Background and Certifications
An Information Security Manager typically holds a degree in information technology, computer science, or cybersecurity, complemented by certifications such as CISSP (Certified Information Systems Security Professional) and CISM (Certified Information Security Manager). A Cybersecurity Manager often has a more specialized educational background focused on network security, cyber defense, or computer engineering, with certifications like CEH (Certified Ethical Hacker), CompTIA Security+, and GIAC Security Essentials (GSEC). Both roles prioritize continuous professional development to stay current with evolving threats and security frameworks.
Scope of Work and Focus Areas
An Information Security Manager oversees the protection of an organization's information assets, focusing on policy development, risk management, and compliance with regulatory standards across all data systems. A Cybersecurity Manager concentrates primarily on defending IT infrastructure from cyber threats, managing security operations, incident response, and vulnerability assessments. While Information Security Managers adopt a broader organizational security strategy, Cybersecurity Managers emphasize technical controls and real-time threat mitigation.
Tools and Technologies Utilized
Information Security Managers primarily utilize risk assessment frameworks, compliance management tools, and data protection technologies such as encryption and access controls to safeguard organizational information assets. Cybersecurity Managers focus on deploying advanced threat detection systems, intrusion prevention tools, and incident response platforms to proactively defend networks and respond to cyber threats. Both roles leverage security information and event management (SIEM) systems and endpoint protection but differ in their emphasis on strategic governance versus operational defense technologies.
Organizational Placement and Reporting Lines
An Information Security Manager typically reports to the Chief Information Officer (CIO) or Chief Risk Officer (CRO), overseeing the organization's policies and compliance related to data protection and regulatory requirements. In contrast, a Cybersecurity Manager often reports to the Chief Information Security Officer (CISO) or Chief Technology Officer (CTO), focusing primarily on technical defenses against cyber threats and incident response. The organizational placement of the Information Security Manager is more aligned with governance and risk management, while the Cybersecurity Manager operates closely within IT departments to handle operational security controls.
Collaboration with Other Departments
Information Security Managers coordinate closely with IT, compliance, and legal departments to align security policies with organizational goals and regulatory requirements. Cybersecurity Managers work alongside network engineers, incident response teams, and software developers to implement technical defenses and respond to cyber threats effectively. Both roles require seamless collaboration across departments to ensure comprehensive protection of digital assets and sensitive information.
Career Path and Advancement Opportunities
Information Security Managers typically oversee organizational policies and compliance frameworks, focusing on risk management and data protection strategies, which positions them for advancement into executive roles like Chief Information Security Officer (CISO). Cybersecurity Managers concentrate on threat detection, incident response, and technical defense mechanisms, often progressing toward specialized leadership roles such as Security Operations Center (SOC) Director or Cybersecurity Architect. Both career paths offer growth opportunities, but Information Security Managers lean toward strategic governance roles, while Cybersecurity Managers advance through technical expertise and operational command.
Salary Expectations and Job Market Trends
Information Security Managers typically earn a median salary ranging from $95,000 to $130,000 annually, reflecting their focus on organizational policies, risk management, and compliance frameworks. Cybersecurity Managers command slightly higher salaries, often between $105,000 and $140,000, driven by increasing demand for expertise in threat analysis, incident response, and advanced cyber defense strategies. Job market trends show robust growth for both roles, but the cybersecurity domain experiences faster expansion due to the rising complexity of cyber threats and regulatory pressures across industries.
Information Security Manager vs Cybersecurity Manager Infographic
 jobdiv.com
jobdiv.com