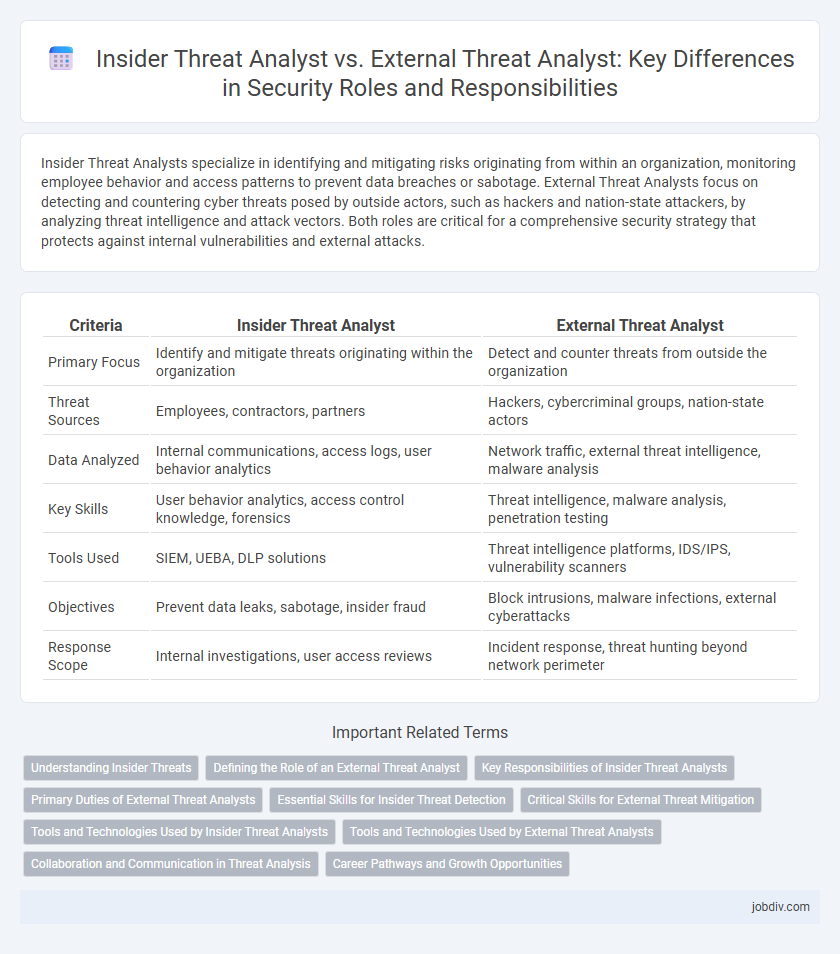
Insider Threat Analysts specialize in identifying and mitigating risks originating from within an organization, monitoring employee behavior and access patterns to prevent data breaches or sabotage. External Threat Analysts focus on detecting and countering cyber threats posed by outside actors, such as hackers and nation-state attackers, by analyzing threat intelligence and attack vectors. Both roles are critical for a comprehensive security strategy that protects against internal vulnerabilities and external attacks.
Table of Comparison
| Criteria | Insider Threat Analyst | External Threat Analyst |
|---|---|---|
| Primary Focus | Identify and mitigate threats originating within the organization | Detect and counter threats from outside the organization |
| Threat Sources | Employees, contractors, partners | Hackers, cybercriminal groups, nation-state actors |
| Data Analyzed | Internal communications, access logs, user behavior analytics | Network traffic, external threat intelligence, malware analysis |
| Key Skills | User behavior analytics, access control knowledge, forensics | Threat intelligence, malware analysis, penetration testing |
| Tools Used | SIEM, UEBA, DLP solutions | Threat intelligence platforms, IDS/IPS, vulnerability scanners |
| Objectives | Prevent data leaks, sabotage, insider fraud | Block intrusions, malware infections, external cyberattacks |
| Response Scope | Internal investigations, user access reviews | Incident response, threat hunting beyond network perimeter |
Understanding Insider Threats
Insider Threat Analysts specialize in identifying risks posed by employees, contractors, and other trusted insiders who have direct access to organizational systems and data, leveraging behavioral analytics and access monitoring tools. Their role emphasizes understanding motivations behind insider actions, including negligence, sabotage, or espionage, to detect subtle indicators of malicious activity. Unlike External Threat Analysts who focus on cyber adversaries outside the network, Insider Threat Analysts prioritize internal vulnerability assessments and insider risk mitigation strategies.
Defining the Role of an External Threat Analyst
An External Threat Analyst specializes in identifying and mitigating cyber threats originating outside the organization, focusing on threat intelligence from hackers, dark web activities, and geopolitical risks. Their responsibilities include monitoring global cyber threat landscapes, analyzing Indicators of Compromise (IOCs), and collaborating with cybersecurity teams to strengthen perimeter defenses. Unlike Insider Threat Analysts who focus on internal risks, External Threat Analysts leverage advanced tools and threat feeds to proactively prevent breaches caused by external actors.
Key Responsibilities of Insider Threat Analysts
Insider Threat Analysts focus on monitoring and analyzing activities within an organization to detect potential threats from employees or contractors, using behavioral analytics, access logs, and anomaly detection. They collaborate with HR and legal teams to investigate suspicious behaviors and enforce security policies to prevent data breaches caused by insiders. Their expertise includes managing insider threat programs, conducting risk assessments, and delivering employee security awareness training to mitigate internal risks.
Primary Duties of External Threat Analysts
External Threat Analysts focus on identifying and mitigating cyber threats originating outside the organization, such as hackers, cybercriminal groups, and state-sponsored actors. They monitor global threat intelligence feeds, analyze malware, and track attack patterns to anticipate and prevent breaches. Their primary duties include vulnerability assessments, threat hunting, and developing strategies to defend against external cyberattacks.
Essential Skills for Insider Threat Detection
Insider Threat Analysts require expertise in behavioral analysis, user activity monitoring, and access control policies to detect subtle signs of malicious intent or negligence within the organization. Proficiency in data correlation, anomaly detection algorithms, and familiarity with insider threat frameworks like CERT and NIST are critical for identifying insider risks. In contrast, External Threat Analysts concentrate more on threat intelligence gathering, cyber attack patterns, and external intrusion detection systems to mitigate risks originating outside the network.
Critical Skills for External Threat Mitigation
Expertise in advanced cyber threat intelligence and real-time monitoring tools is crucial for External Threat Analysts to detect and mitigate sophisticated attacks from outside the organization. Proficiency in threat hunting, incident response, and understanding of global threat actor tactics enables effective prevention of data breaches and system infiltrations. Strong skills in vulnerability assessment and knowledge of emerging external threat landscapes also enhance the ability to safeguard organizational assets.
Tools and Technologies Used by Insider Threat Analysts
Insider Threat Analysts utilize behavioral analytics platforms, such as User and Entity Behavior Analytics (UEBA) tools, to detect anomalies within employee activities that may indicate malicious intent or policy violations. They rely on Data Loss Prevention (DLP) systems, endpoint monitoring software, and Security Information and Event Management (SIEM) solutions to gather, correlate, and analyze internal data for suspicious patterns. Advanced insider threat programs often incorporate machine learning algorithms and access control technologies to proactively identify and mitigate risks posed by trusted personnel.
Tools and Technologies Used by External Threat Analysts
External Threat Analysts primarily use advanced threat intelligence platforms, network security monitoring tools, and open-source intelligence (OSINT) frameworks to identify and mitigate risks originating outside the organization. They rely heavily on Security Information and Event Management (SIEM) systems, intrusion detection systems (IDS), and automated vulnerability scanners to detect external attacks and suspicious activity. Integration of machine learning algorithms and real-time data analytics enhances their ability to predict and respond to emerging cyber threats efficiently.
Collaboration and Communication in Threat Analysis
Insider Threat Analysts and External Threat Analysts enhance organizational security by sharing intelligence on threat indicators and behavioral patterns, enabling more comprehensive threat detection. Collaborative communication channels between these roles facilitate real-time exchange of insights about internal vulnerabilities and external attack vectors. This synergy improves incident response times and strengthens overall threat mitigation strategies.
Career Pathways and Growth Opportunities
Insider Threat Analysts specialize in identifying and mitigating risks originating from within an organization, focusing on employee behavior, access controls, and internal system monitoring, which often leads to career advancement in roles such as Security Operations Center (SOC) Manager or Chief Information Security Officer (CISO). External Threat Analysts concentrate on detecting and defending against cyberattacks from outside sources, analyzing malware, phishing campaigns, and threat intelligence feeds, with growth opportunities in threat intelligence leadership and cybersecurity consulting. Both career paths offer specialization in different threat vectors, and cross-training can enhance prospects in broader cybersecurity management and risk assessment roles.
Insider Threat Analyst vs External Threat Analyst Infographic
 jobdiv.com
jobdiv.com