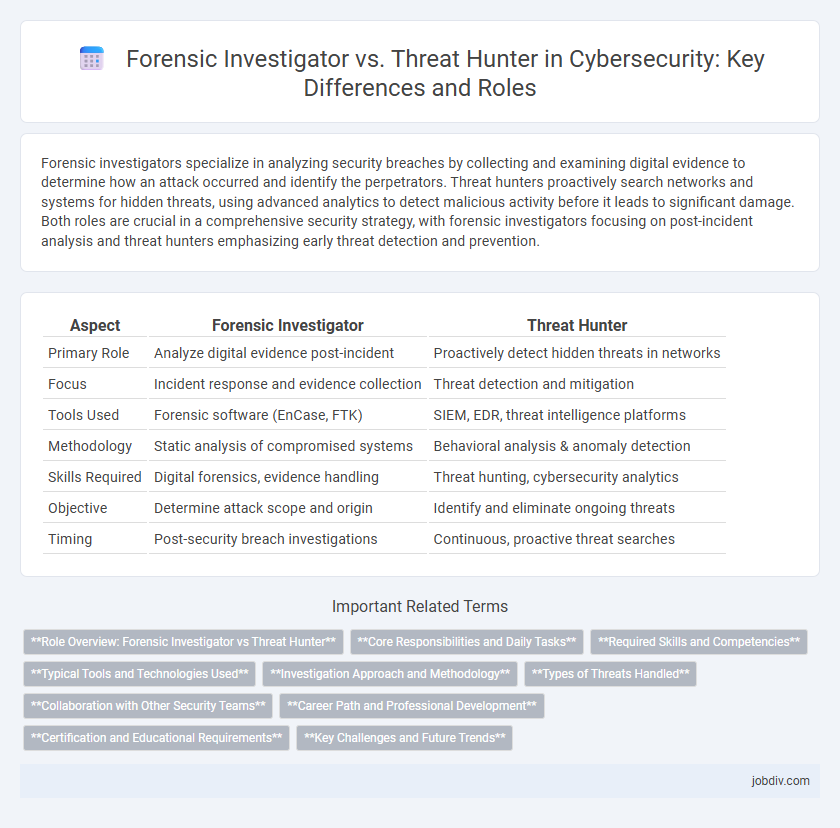
Forensic investigators specialize in analyzing security breaches by collecting and examining digital evidence to determine how an attack occurred and identify the perpetrators. Threat hunters proactively search networks and systems for hidden threats, using advanced analytics to detect malicious activity before it leads to significant damage. Both roles are crucial in a comprehensive security strategy, with forensic investigators focusing on post-incident analysis and threat hunters emphasizing early threat detection and prevention.
Table of Comparison
| Aspect | Forensic Investigator | Threat Hunter |
|---|---|---|
| Primary Role | Analyze digital evidence post-incident | Proactively detect hidden threats in networks |
| Focus | Incident response and evidence collection | Threat detection and mitigation |
| Tools Used | Forensic software (EnCase, FTK) | SIEM, EDR, threat intelligence platforms |
| Methodology | Static analysis of compromised systems | Behavioral analysis & anomaly detection |
| Skills Required | Digital forensics, evidence handling | Threat hunting, cybersecurity analytics |
| Objective | Determine attack scope and origin | Identify and eliminate ongoing threats |
| Timing | Post-security breach investigations | Continuous, proactive threat searches |
Role Overview: Forensic Investigator vs Threat Hunter
Forensic Investigators specialize in collecting, preserving, and analyzing digital evidence to uncover the cause and impact of security incidents, ensuring chain-of-custody for legal proceedings. Threat Hunters proactively search for hidden threats and indicators of compromise within an organization's network to detect and mitigate cyber threats before they cause harm. Both roles require deep knowledge of cybersecurity tools and techniques, but Forensic Investigators focus on post-incident analysis while Threat Hunters emphasize real-time detection and prevention.
Core Responsibilities and Daily Tasks
Forensic investigators primarily focus on collecting, preserving, and analyzing digital evidence from compromised systems to support legal proceedings and incident response. Threat hunters proactively search networks and systems for hidden threats and indicators of compromise that evade automated detection tools. Both roles require deep knowledge of malware analysis, log examination, and cybersecurity frameworks, but forensic investigators emphasize post-incident investigation while threat hunters prioritize real-time detection and prevention.
Required Skills and Competencies
Forensic investigators require expertise in digital evidence collection, chain of custody management, and deep knowledge of operating systems, file systems, and forensic tools like EnCase or FTK. Threat hunters must possess advanced skills in threat intelligence, behavioral analytics, intrusion detection, and proficiency with SIEM platforms and scripting languages such as Python or PowerShell. Both roles demand strong analytical thinking, attention to detail, and a solid understanding of cybersecurity frameworks and incident response methodologies.
Typical Tools and Technologies Used
Forensic investigators primarily use tools like EnCase, FTK, and Autopsy to collect and analyze digital evidence from compromised systems, focusing on data preservation and detailed reporting. Threat hunters leverage platforms such as Splunk, CrowdStrike Falcon, and Endpoint Detection and Response (EDR) tools to proactively detect and mitigate threats by analyzing real-time telemetry and behavior analytics. Both roles rely heavily on network traffic analysis, but forensic investigators emphasize post-incident examination while threat hunters prioritize continuous threat detection and response.
Investigation Approach and Methodology
Forensic investigators employ a systematic approach centered on evidence collection, preservation, and analysis to reconstruct past cyber incidents, often relying on chain-of-custody protocols and detailed documentation. Threat hunters utilize proactive, hypothesis-driven methodologies that combine threat intelligence, behavioral analytics, and anomaly detection to identify and mitigate potential threats before they cause damage. Both roles leverage advanced tools--digital forensics suites for investigators and continuous monitoring platforms for hunters--to enhance detection accuracy and response effectiveness.
Types of Threats Handled
Forensic Investigators primarily handle post-incident threats such as data breaches, malware infections, and insider threats by analyzing digital evidence to determine attack vectors and impact. Threat Hunters focus on proactive detection of advanced persistent threats (APTs), zero-day exploits, and evolving malware by continuously monitoring and analyzing network traffic and system behaviors. Both roles address complex cyber threats but differ in timing, with Forensic Investigators responding after an attack and Threat Hunters seeking to identify threats before they cause significant damage.
Collaboration with Other Security Teams
Forensic investigators collaborate closely with incident response and legal teams to analyze evidence and support prosecution, ensuring chain of custody and compliance with regulations. Threat hunters work alongside security operations centers (SOCs) and malware analysts to proactively identify and mitigate advanced threats through continuous monitoring and anomaly detection. Their joint efforts enhance the overall security posture by combining reactive investigation with proactive threat detection.
Career Path and Professional Development
Forensic Investigators typically advance through certifications like CFCE and EnCE, gaining expertise in digital evidence collection and legal compliance, often transitioning to roles such as Incident Response Lead or Cybercrime Analyst. Threat Hunters develop skills in threat intelligence, malware analysis, and behavioral analytics, supported by certifications like GCIA and GREM, progressing towards positions like Threat Intelligence Manager or Security Operations Center (SOC) Director. Continuous learning through hands-on incident simulations and up-to-date knowledge of evolving cyber threats is crucial for career growth in both fields.
Certification and Educational Requirements
Forensic Investigators typically require certifications such as Certified Computer Examiner (CCE) or GIAC Certified Forensic Analyst (GCFA), along with a background in digital forensics, cybersecurity, or criminal justice. Threat Hunters often pursue certifications like Certified Threat Intelligence Analyst (CTIA) or GIAC Cyber Threat Intelligence (GCTI), emphasizing expertise in threat detection, analysis, and incident response. Both roles benefit from a strong foundation in computer science or information security, but certifications validate specialized skills aligned with their distinct operational focuses.
Key Challenges and Future Trends
Forensic investigators face challenges in handling increasingly sophisticated data encryption and ensuring the integrity of digital evidence amid growing privacy regulations. Threat hunters must continuously adapt to evolving attack techniques and deploy advanced AI-driven analytics to proactively detect hidden threats within complex network environments. Emerging trends emphasize the integration of machine learning for real-time anomaly detection and the convergence of forensic and threat hunting disciplines to enhance incident response effectiveness.
Forensic Investigator vs Threat Hunter Infographic
 jobdiv.com
jobdiv.com