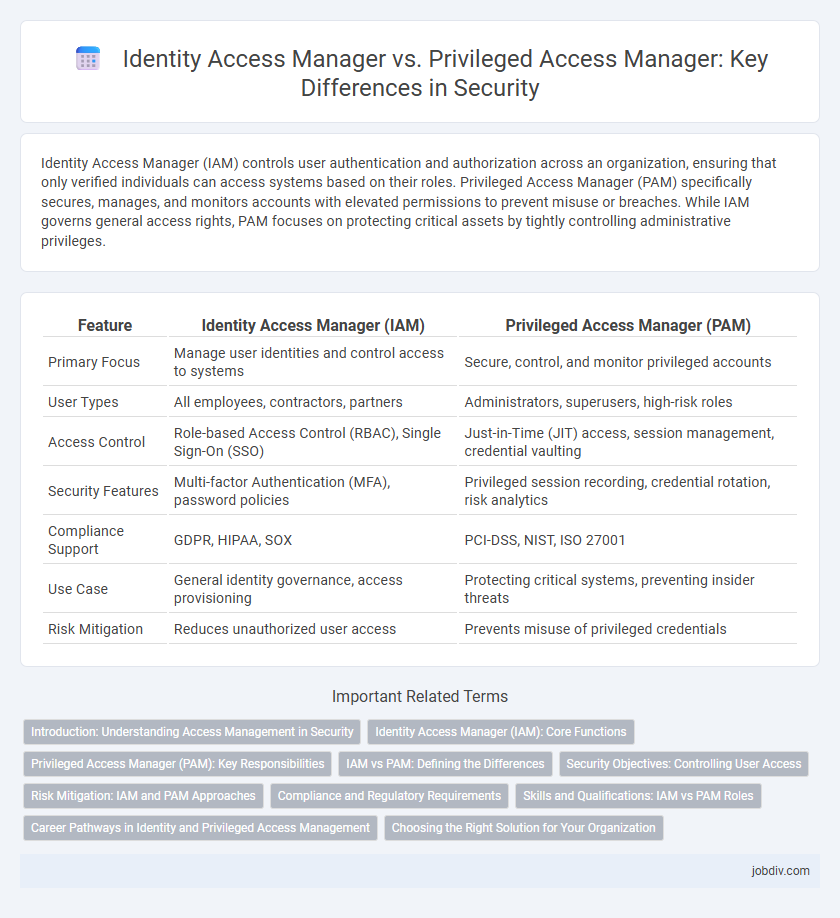
Identity Access Manager (IAM) controls user authentication and authorization across an organization, ensuring that only verified individuals can access systems based on their roles. Privileged Access Manager (PAM) specifically secures, manages, and monitors accounts with elevated permissions to prevent misuse or breaches. While IAM governs general access rights, PAM focuses on protecting critical assets by tightly controlling administrative privileges.
Table of Comparison
| Feature | Identity Access Manager (IAM) | Privileged Access Manager (PAM) |
|---|---|---|
| Primary Focus | Manage user identities and control access to systems | Secure, control, and monitor privileged accounts |
| User Types | All employees, contractors, partners | Administrators, superusers, high-risk roles |
| Access Control | Role-based Access Control (RBAC), Single Sign-On (SSO) | Just-in-Time (JIT) access, session management, credential vaulting |
| Security Features | Multi-factor Authentication (MFA), password policies | Privileged session recording, credential rotation, risk analytics |
| Compliance Support | GDPR, HIPAA, SOX | PCI-DSS, NIST, ISO 27001 |
| Use Case | General identity governance, access provisioning | Protecting critical systems, preventing insider threats |
| Risk Mitigation | Reduces unauthorized user access | Prevents misuse of privileged credentials |
Introduction: Understanding Access Management in Security
Identity Access Manager (IAM) and Privileged Access Manager (PAM) are critical components of access management in cybersecurity, each serving distinct roles. IAM focuses on managing user identities and their access rights across systems to ensure appropriate authorization and prevent unauthorized access. PAM specifically controls and monitors access to critical systems and sensitive data by privileged users, reducing the risk of insider threats and credential abuse.
Identity Access Manager (IAM): Core Functions
Identity Access Manager (IAM) primarily controls user access by verifying identities, managing credentials, and enforcing authentication policies across systems. Core functions include user provisioning, role-based access control (RBAC), single sign-on (SSO), and self-service password management to ensure secure and efficient identity lifecycle management. IAM reduces security risks by maintaining compliance with regulations, preventing unauthorized access, and enabling detailed audit trails of user activities.
Privileged Access Manager (PAM): Key Responsibilities
Privileged Access Manager (PAM) is essential for controlling and monitoring elevated access to critical systems, reducing the risk of insider threats and external cyberattacks. PAM enforces least privilege access, manages privileged credentials, and records all privileged session activities to ensure accountability and compliance. Effective PAM deployment integrates with Identity Access Manager (IAM) but focuses specifically on securing, auditing, and controlling access to sensitive assets.
IAM vs PAM: Defining the Differences
Identity Access Manager (IAM) governs user authentication and authorization across an organization, managing general user access to systems and applications. Privileged Access Manager (PAM) focuses specifically on securing, monitoring, and controlling elevated accounts with critical system privileges to prevent unauthorized access and reduce insider threats. While IAM provides broad access management for all users, PAM enforces stricter controls on privileged identities to ensure critical resource protection and regulatory compliance.
Security Objectives: Controlling User Access
Identity Access Manager (IAM) enforces user authentication and authorization policies to ensure that only legitimate users have access to systems and data, minimizing unauthorized access risks. Privileged Access Manager (PAM) specifically controls and monitors elevated or administrative privileges, reducing the attack surface by securing critical accounts and preventing privilege misuse. Together, IAM addresses broad user access control, while PAM focuses on safeguarding high-risk privileged accounts to enhance overall security posture.
Risk Mitigation: IAM and PAM Approaches
Identity Access Manager (IAM) frameworks mitigate risk by enforcing organization-wide authentication policies, role-based access controls, and continuous user behavior monitoring to prevent unauthorized access. Privileged Access Manager (PAM) solutions focus on securing, controlling, and auditing elevated account activities, using just-in-time access and session recording to reduce insider threats and credential exploitation. Both IAM and PAM are essential for a layered defense strategy, with IAM addressing broad user access risks and PAM targeting high-value account vulnerabilities.
Compliance and Regulatory Requirements
Identity Access Manager (IAM) enforces user authentication and access permissions across enterprise systems, ensuring compliance with regulations like GDPR and HIPAA by maintaining detailed audit trails and role-based access controls. Privileged Access Manager (PAM) specializes in securing, monitoring, and controlling access to elevated accounts, critical for meeting stricter compliance standards such as PCI-DSS and SOX by preventing unauthorized use of privileged credentials. Both IAM and PAM are essential for comprehensive regulatory compliance, minimizing risks related to identity misuse and ensuring adherence to legal and industry-specific security mandates.
Skills and Qualifications: IAM vs PAM Roles
Identity Access Manager (IAM) professionals require expertise in user lifecycle management, role-based access control, and compliance frameworks like GDPR and HIPAA to ensure secure and efficient identity governance. Privileged Access Manager (PAM) specialists must possess advanced skills in managing and monitoring privileged accounts, implementing just-in-time access, and deploying threat detection tools to protect critical assets from insider and external threats. Both roles demand strong knowledge of security protocols, identity federation technologies, and audit practices, but PAM focuses more intensively on risk mitigation for high-level permissions within enterprise environments.
Career Pathways in Identity and Privileged Access Management
Identity Access Manager roles focus on managing user access rights and ensuring compliance across IT systems, emphasizing skills in identity governance and access control frameworks. Privileged Access Manager careers require expertise in securing high-level credentials, implementing least privilege policies, and monitoring privileged user activities to prevent internal threats. Both pathways offer growth in cybersecurity, with Privileged Access Management roles often commanding higher salaries due to the critical nature of safeguarding sensitive access.
Choosing the Right Solution for Your Organization
Identity Access Manager (IAM) focuses on managing and authenticating user identities across an entire organization, ensuring appropriate access to systems and applications. Privileged Access Manager (PAM) specifically secures and monitors the use of elevated or administrative accounts, mitigating risks associated with high-level access. Organizations should evaluate the scope of access control needs, the sensitivity of privileged accounts, and compliance requirements to determine whether IAM, PAM, or an integrated approach best aligns with their security strategy.
Identity Access Manager vs Privileged Access Manager Infographic
 jobdiv.com
jobdiv.com