Red Team Operators simulate cyberattacks to identify vulnerabilities and test an organization's defenses, using offensive tactics and techniques to mimic real-world threats. Blue Team Analysts focus on defending systems by monitoring networks, analyzing security data, and responding to incidents to prevent breaches and mitigate damage. Both roles are essential in a comprehensive security strategy, balancing proactive offense with vigilant defense.
Table of Comparison
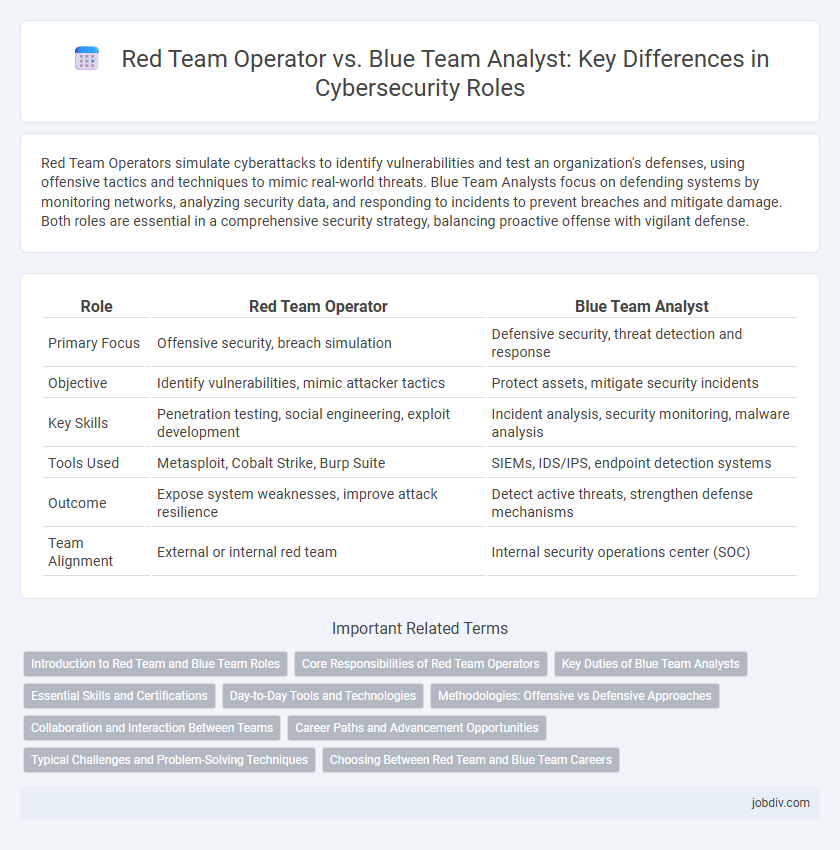
| Role | Red Team Operator | Blue Team Analyst |
|---|---|---|
| Primary Focus | Offensive security, breach simulation | Defensive security, threat detection and response |
| Objective | Identify vulnerabilities, mimic attacker tactics | Protect assets, mitigate security incidents |
| Key Skills | Penetration testing, social engineering, exploit development | Incident analysis, security monitoring, malware analysis |
| Tools Used | Metasploit, Cobalt Strike, Burp Suite | SIEMs, IDS/IPS, endpoint detection systems |
| Outcome | Expose system weaknesses, improve attack resilience | Detect active threats, strengthen defense mechanisms |
| Team Alignment | External or internal red team | Internal security operations center (SOC) |
Introduction to Red Team and Blue Team Roles
Red Team Operators simulate real-world cyber attacks to identify vulnerabilities and test an organization's security defenses, emphasizing offensive techniques like penetration testing and social engineering. Blue Team Analysts focus on defensive measures by monitoring networks, analyzing threats, and implementing incident response strategies to protect against intrusions. Together, these roles create a comprehensive security framework by balancing proactive attack simulation with robust defense mechanisms.
Core Responsibilities of Red Team Operators
Red Team Operators specialize in simulating adversarial attacks to identify vulnerabilities in organizational security frameworks. They conduct comprehensive penetration testing, exploit weaknesses, and mimic real-world threat scenarios to enhance defense mechanisms. Their core responsibility involves providing actionable intelligence that drives proactive security improvements and resilience against cyber threats.
Key Duties of Blue Team Analysts
Blue Team Analysts specialize in continuous monitoring and threat detection to protect organizational networks from cyberattacks. They conduct vulnerability assessments, implement security measures, and manage incident response protocols to minimize damage and recover quickly. Their key duties also include analyzing security logs, maintaining firewalls, and ensuring compliance with cybersecurity policies and standards.
Essential Skills and Certifications
Red Team Operators require advanced offensive cybersecurity skills such as penetration testing, social engineering, and exploit development, often validated by certifications like OSCP (Offensive Security Certified Professional) and CEH (Certified Ethical Hacker). Blue Team Analysts focus on defensive tactics, including threat detection, incident response, and log analysis, with certifications such as CISSP (Certified Information Systems Security Professional) and CISM (Certified Information Security Manager) emphasizing their expertise. Both roles demand deep knowledge of network protocols, vulnerability assessment, and real-time security monitoring to effectively simulate attacks or protect organizational assets.
Day-to-Day Tools and Technologies
Red Team Operators rely heavily on offensive security tools such as Metasploit, Cobalt Strike, and custom exploit frameworks to simulate real-world attacks and identify vulnerabilities. Blue Team Analysts utilize defensive technologies including Security Information and Event Management (SIEM) systems like Splunk or IBM QRadar, Intrusion Detection Systems (IDS), Endpoint Detection and Response (EDR) solutions, and network traffic analysis tools to monitor, detect, and respond to threats in real-time. Both roles require deep expertise in scripting languages and threat intelligence platforms to effectively carry out their daily cybersecurity tasks.
Methodologies: Offensive vs Defensive Approaches
Red Team Operators employ offensive methodologies such as penetration testing, social engineering, and vulnerability exploitation to simulate real-world cyberattacks and identify security weaknesses. Blue Team Analysts focus on defensive strategies including continuous network monitoring, incident response, threat detection, and implementing security controls to protect organizational assets. The contrasting approaches emphasize proactive attack simulation by Red Teams versus resilient defense and mitigation tactics by Blue Teams in cybersecurity operations.
Collaboration and Interaction Between Teams
Red Team Operators simulate cyberattacks to identify vulnerabilities, while Blue Team Analysts defend networks and analyze threats in real time. Effective collaboration between these teams enhances threat detection by combining offensive insights with defensive strategies. Regular interaction through joint exercises and debriefs fosters knowledge sharing, improves response protocols, and strengthens overall organizational cybersecurity.
Career Paths and Advancement Opportunities
Red Team Operators specialize in offensive security, developing skills in penetration testing, social engineering, and vulnerability exploitation, often advancing to roles like Ethical Hacker or Security Consultant. Blue Team Analysts focus on defensive tactics, including threat detection, incident response, and security monitoring, with career growth leading to positions such as Security Operations Center (SOC) Manager or Cybersecurity Analyst. Both paths offer opportunities for certifications like OSCP for Red Team and CISSP for Blue Team, enhancing advancement potential within cybersecurity leadership.
Typical Challenges and Problem-Solving Techniques
Red Team Operators face challenges such as simulating realistic attack vectors and bypassing advanced defense mechanisms to identify system vulnerabilities. Blue Team Analysts must detect, analyze, and respond to these penetration attempts in real-time, often relying on continuous monitoring and threat intelligence platforms. Effective problem-solving involves Red Teams employing adaptive tactics and stealth techniques, while Blue Teams leverage automated alerting systems, forensic analysis, and incident response protocols to strengthen organizational security.
Choosing Between Red Team and Blue Team Careers
Red Team Operators simulate cyberattacks to identify vulnerabilities and test an organization's defenses, requiring deep expertise in offensive security techniques and threat emulation. Blue Team Analysts focus on monitoring, detecting, and responding to cybersecurity incidents, emphasizing skills in threat analysis, incident response, and defensive strategy implementation. Choosing between Red Team and Blue Team careers depends on whether you prefer proactive adversary simulation or reactive defense and mitigation within cybersecurity operations.
Red Team Operator vs Blue Team Analyst Infographic
 jobdiv.com
jobdiv.com