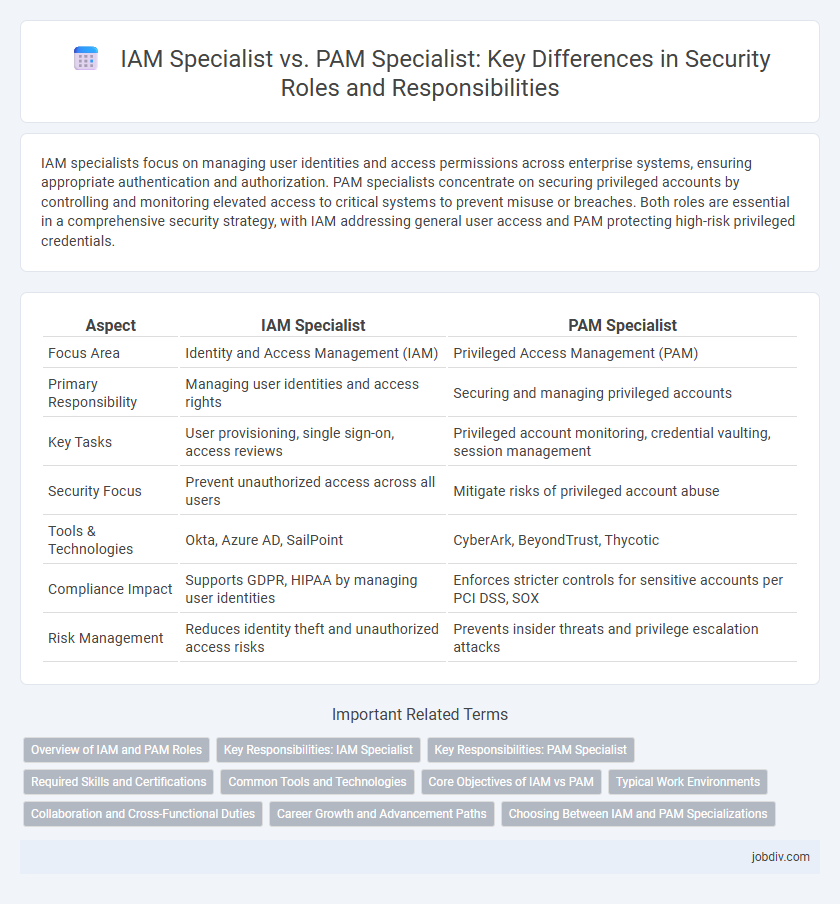
IAM specialists focus on managing user identities and access permissions across enterprise systems, ensuring appropriate authentication and authorization. PAM specialists concentrate on securing privileged accounts by controlling and monitoring elevated access to critical systems to prevent misuse or breaches. Both roles are essential in a comprehensive security strategy, with IAM addressing general user access and PAM protecting high-risk privileged credentials.
Table of Comparison
| Aspect | IAM Specialist | PAM Specialist |
|---|---|---|
| Focus Area | Identity and Access Management (IAM) | Privileged Access Management (PAM) |
| Primary Responsibility | Managing user identities and access rights | Securing and managing privileged accounts |
| Key Tasks | User provisioning, single sign-on, access reviews | Privileged account monitoring, credential vaulting, session management |
| Security Focus | Prevent unauthorized access across all users | Mitigate risks of privileged account abuse |
| Tools & Technologies | Okta, Azure AD, SailPoint | CyberArk, BeyondTrust, Thycotic |
| Compliance Impact | Supports GDPR, HIPAA by managing user identities | Enforces stricter controls for sensitive accounts per PCI DSS, SOX |
| Risk Management | Reduces identity theft and unauthorized access risks | Prevents insider threats and privilege escalation attacks |
Overview of IAM and PAM Roles
IAM specialists manage user identities and access permissions across systems, ensuring proper authentication and authorization to protect organizational assets. PAM specialists focus specifically on controlling and monitoring privileged accounts, reducing the risk of insider threats and preventing unauthorized access to critical systems. Both roles are essential for comprehensive identity security, with IAM covering broader user access while PAM targets elevated privilege management.
Key Responsibilities: IAM Specialist
IAM Specialists manage user identities and access permissions across enterprise systems, ensuring secure authentication and governance. They implement role-based access controls and maintain identity lifecycle processes to prevent unauthorized access. Continuous monitoring and compliance enforcement within identity and access management frameworks are critical aspects of their role.
Key Responsibilities: PAM Specialist
PAM Specialists manage privileged access by implementing and maintaining robust controls to prevent unauthorized use of high-level accounts, ensuring compliance with security policies. They conduct regular audits, monitor privileged session activities, and respond to access anomalies to mitigate insider threats. Their role includes integrating PAM solutions with existing Identity and Access Management (IAM) frameworks to enhance overall security posture.
Required Skills and Certifications
An IAM Specialist requires in-depth knowledge of identity lifecycle management, role-based access control, and federated identity protocols, with certifications such as Certified Identity and Access Manager (CIAM) and Microsoft Certified: Identity and Access Administrator Associate enhancing credibility. In contrast, a PAM Specialist must excel in privileged account discovery, session monitoring, and threat detection, often holding credentials like CyberArk Certified Trustee or BeyondTrust Certified PAM Specialist. Both roles demand strong understanding of security frameworks and compliance standards, but PAM emphasizes managing and securing high-risk privileged accounts more intensively.
Common Tools and Technologies
IAM specialists commonly use tools like Microsoft Azure Active Directory, Okta, and SailPoint to manage identity lifecycle and access governance. PAM specialists focus on technologies such as CyberArk, BeyondTrust, and Thycotic for privileged account discovery, session monitoring, and credential vaulting. Both roles leverage multi-factor authentication (MFA) and single sign-on (SSO) solutions but apply them within distinct scopes of identity versus privileged access management.
Core Objectives of IAM vs PAM
IAM specialists focus on managing digital identities, ensuring users have appropriate access rights based on roles to protect organizational assets and streamline user authentication processes. PAM specialists concentrate on controlling and monitoring privileged accounts, minimizing the risk of excessive access and potential breaches by enforcing strict oversight and session management. Core objectives of IAM involve identity verification and access governance, while PAM centers on securing, managing, and auditing privileged credentials to prevent insider threats and credential abuse.
Typical Work Environments
IAM Specialists typically work in corporate IT departments, managed security service providers (MSSPs), and government agencies where identity verification and access management are critical. PAM Specialists are often found in financial institutions, healthcare organizations, and large enterprises with stringent privileged account controls and compliance requirements. Both roles frequently collaborate in environments emphasizing robust cybersecurity frameworks and regulatory adherence.
Collaboration and Cross-Functional Duties
IAM Specialists collaborate closely with IT, compliance, and security teams to design and implement identity management frameworks that ensure secure and efficient access control across enterprise systems. PAM Specialists work in tandem with system administrators and security operations to manage privileged accounts, focusing on monitoring, controlling, and auditing elevated access to prevent insider threats and credential misuse. Both roles require cross-functional coordination to align identity and privilege access strategies with organizational security policies and risk management objectives.
Career Growth and Advancement Paths
IAM Specialists typically advance by mastering identity lifecycle management, access governance, and regulatory compliance, leading to roles such as Identity Architect or Security Manager. PAM Specialists progress through expertise in privileged account security, session monitoring, and risk mitigation, often advancing to positions like PAM Consultant or Chief Security Officer. Both career paths offer strong growth potential, with IAM roles focusing on broad identity frameworks and PAM careers emphasizing critical risk management within enterprise security.
Choosing Between IAM and PAM Specializations
Choosing between IAM and PAM specializations depends on organizational security priorities: IAM specialists manage user identities and access rights across systems, ensuring proper authentication and authorization, while PAM specialists focus on securing, monitoring, and managing privileged accounts to prevent insider threats and unauthorized access. Organizations with complex user hierarchies and broad access requirements benefit from IAM expertise for efficient identity lifecycle management. In contrast, environments with high-value assets and critical infrastructure demand PAM specialists to safeguard privileged credentials and implement strict access controls.
IAM Specialist vs PAM Specialist Infographic
 jobdiv.com
jobdiv.com