A Digital Forensics Examiner specializes in recovering and analyzing data from compromised devices to uncover evidence of cybercrimes, ensuring digital trails are preserved for legal proceedings. A Malware Analyst focuses on identifying, dissecting, and understanding malicious software to develop effective countermeasures and protect systems from future attacks. Both roles are critical in cybersecurity, but the examiner emphasizes post-incident investigation while the analyst concentrates on proactive malware threat mitigation.
Table of Comparison
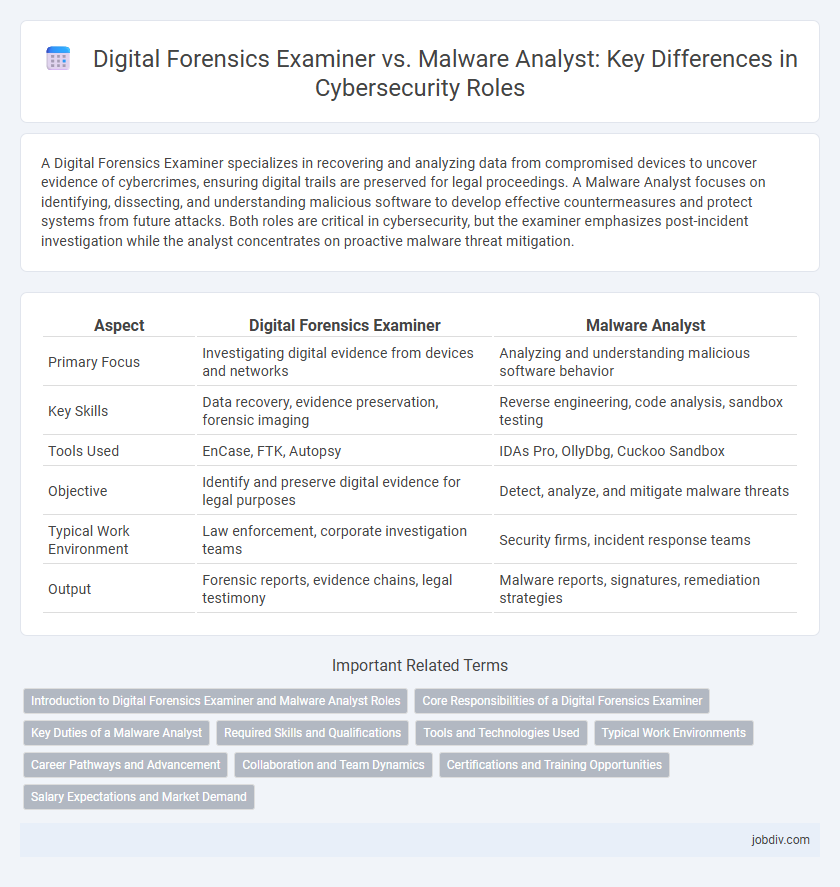
| Aspect | Digital Forensics Examiner | Malware Analyst |
|---|---|---|
| Primary Focus | Investigating digital evidence from devices and networks | Analyzing and understanding malicious software behavior |
| Key Skills | Data recovery, evidence preservation, forensic imaging | Reverse engineering, code analysis, sandbox testing |
| Tools Used | EnCase, FTK, Autopsy | IDAs Pro, OllyDbg, Cuckoo Sandbox |
| Objective | Identify and preserve digital evidence for legal purposes | Detect, analyze, and mitigate malware threats |
| Typical Work Environment | Law enforcement, corporate investigation teams | Security firms, incident response teams |
| Output | Forensic reports, evidence chains, legal testimony | Malware reports, signatures, remediation strategies |
Introduction to Digital Forensics Examiner and Malware Analyst Roles
Digital Forensics Examiners specialize in collecting, preserving, and analyzing digital evidence from electronic devices to support legal investigations. Malware Analysts focus on identifying, dissecting, and understanding malicious software to develop mitigation strategies and protect information systems. Both roles play critical parts in cybersecurity by uncovering digital threats and ensuring data integrity during incident response.
Core Responsibilities of a Digital Forensics Examiner
A Digital Forensics Examiner specializes in recovering, preserving, and analyzing digital evidence from various devices to support criminal investigations and cybersecurity incidents. Their core responsibilities include imaging storage media, conducting file system analysis, and preparing detailed reports that maintain the chain of custody for use in legal proceedings. Unlike Malware Analysts who focus on dissecting malicious code, Digital Forensics Examiners ensure data integrity and trace the source and impact of security breaches through comprehensive digital investigations.
Key Duties of a Malware Analyst
Malware analysts specialize in identifying, dissecting, and understanding malicious software to mitigate cyber threats and protect organizational assets. Their key duties involve reverse engineering malware code to reveal its functionality, behavior analysis to determine infection vectors and payload impact, and developing detection signatures for security tools like antivirus software. These experts also collaborate with incident response teams to support remediation efforts and enhance overall cybersecurity resilience.
Required Skills and Qualifications
Digital Forensics Examiners require expertise in evidence collection, chain of custody procedures, and proficiency with forensic tools like EnCase and FTK, along with certifications such as CFCE or GCFA. Malware Analysts need strong skills in reverse engineering, programming languages like C++ and Python, and familiarity with sandbox environments and debugging tools such as IDA Pro or OllyDbg, supported by certifications like GREM or CEH. Both roles demand a solid understanding of operating systems, networking, and cybersecurity principles to effectively analyze and mitigate digital threats.
Tools and Technologies Used
Digital Forensics Examiners utilize tools like EnCase, FTK, and Autopsy to recover and analyze data from digital devices, focusing on evidence preservation and chain of custody. Malware Analysts rely on sandbox environments, IDA Pro, and dynamic analysis tools such as Cuckoo Sandbox to dissect malicious software behavior and code. Both roles depend on specialized software but differ in their primary focus: forensic evidence recovery versus malware behavior analysis.
Typical Work Environments
Digital Forensics Examiners primarily work in law enforcement agencies, cybersecurity firms, and corporate security departments, analyzing digital evidence to support investigations and legal proceedings. Malware Analysts operate mainly in cybersecurity companies, incident response teams, and research labs, focusing on studying malicious software to develop detection and mitigation strategies. Both roles often require access to secure lab environments equipped with advanced analytical tools and isolated networks to prevent unintended malware propagation.
Career Pathways and Advancement
Digital Forensics Examiners specialize in recovering and investigating data from digital devices to support legal cases, often advancing to roles such as forensic consultants or cybersecurity managers. Malware Analysts focus on dissecting malicious software to understand its behavior and develop mitigation strategies, typically progressing to positions like threat intelligence analysts or malware research leads. Both career paths offer opportunities for specialization and leadership within cybersecurity, with growing demand driven by increasing cybercrime complexity and evolving threat landscapes.
Collaboration and Team Dynamics
Digital Forensics Examiners and Malware Analysts collaborate closely to enhance cybersecurity incident response, with examiners focusing on evidence collection and analysts specializing in malware behavior analysis. Effective team dynamics emerge from their complementary skills, enabling rapid identification, containment, and remediation of cyber threats. Shared knowledge platforms and continuous communication streamline workflows, ensuring comprehensive threat mitigation and forensic accuracy.
Certifications and Training Opportunities
Digital Forensics Examiners often pursue certifications like Certified Forensic Computer Examiner (CFCE) and GIAC Certified Forensic Analyst (GCFA), which emphasize skills in evidence collection and legal standards. Malware Analysts typically obtain credentials such as GIAC Reverse Engineering Malware (GREM) and Offensive Security Certified Professional (OSCP) that focus on dissecting malicious code and threat mitigation. Training opportunities for both roles include specialized courses from SANS Institute, Cybersecurity and Infrastructure Security Agency (CISA) workshops, and hands-on labs through platforms like Cyber Aces and Cybrary.
Salary Expectations and Market Demand
Digital Forensics Examiners typically command salaries ranging from $70,000 to $120,000 annually, driven by the growing need to investigate cybercrimes and retrieve digital evidence. Malware Analysts often see comparable or slightly higher salary brackets, between $75,000 and $130,000, due to their expertise in identifying, dissecting, and mitigating malicious software threats. Market demand remains strong for both roles, with Malware Analysts experiencing heightened growth as organizations prioritize proactive threat detection and incident response capabilities.
Digital Forensics Examiner vs Malware Analyst Infographic
 jobdiv.com
jobdiv.com