Red Team simulates cyberattacks to identify vulnerabilities and test the effectiveness of an organization's security defenses. Blue Team strengthens security by detecting, responding to, and mitigating threats in real-time, maintaining robust protection against potential breaches. Collaboration between Red and Blue Teams enhances overall cybersecurity resilience by promoting continuous improvement and adaptive defense strategies.
Table of Comparison
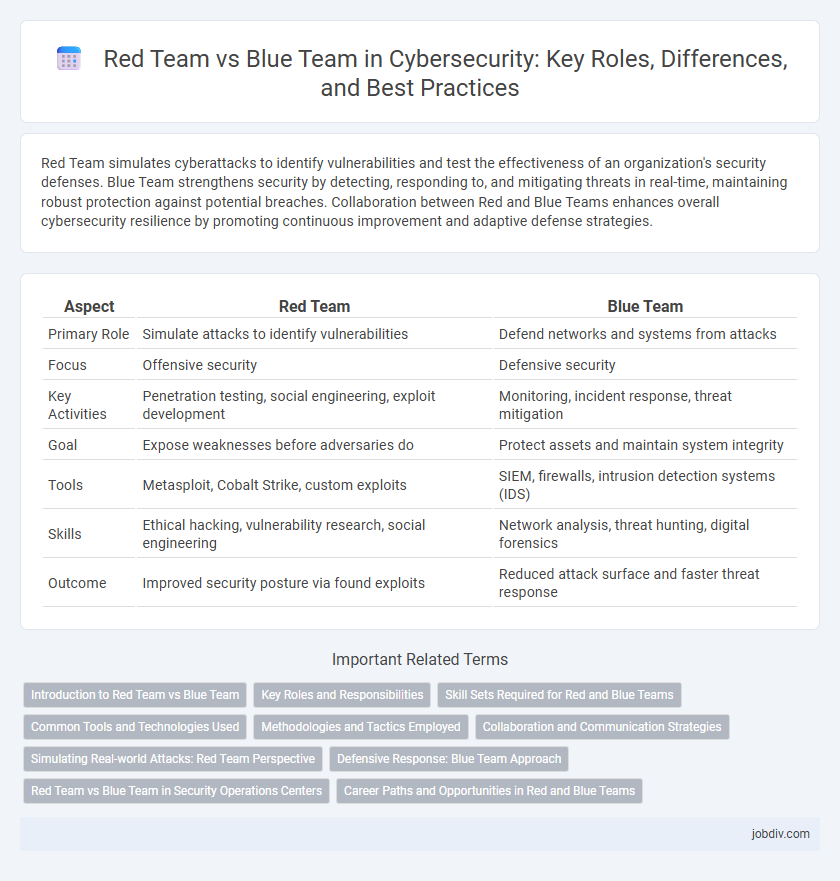
| Aspect | Red Team | Blue Team |
|---|---|---|
| Primary Role | Simulate attacks to identify vulnerabilities | Defend networks and systems from attacks |
| Focus | Offensive security | Defensive security |
| Key Activities | Penetration testing, social engineering, exploit development | Monitoring, incident response, threat mitigation |
| Goal | Expose weaknesses before adversaries do | Protect assets and maintain system integrity |
| Tools | Metasploit, Cobalt Strike, custom exploits | SIEM, firewalls, intrusion detection systems (IDS) |
| Skills | Ethical hacking, vulnerability research, social engineering | Network analysis, threat hunting, digital forensics |
| Outcome | Improved security posture via found exploits | Reduced attack surface and faster threat response |
Introduction to Red Team vs Blue Team
Red Team and Blue Team represent two fundamental roles in cybersecurity aimed at enhancing organizational defenses. The Red Team simulates realistic cyberattacks to identify vulnerabilities and test the security posture, while the Blue Team is responsible for detecting, responding to, and mitigating such threats in real time. Together, these teams create a dynamic framework for continuous security improvement and threat resilience.
Key Roles and Responsibilities
Red Team focuses on offensive security by simulating cyberattacks to identify vulnerabilities, testing an organization's defenses through penetration testing and social engineering. Blue Team specializes in defensive security, responsible for monitoring systems, detecting intrusions, and responding to threats to protect the network infrastructure. Key responsibilities for Red Team include vulnerability assessment and attack simulation, while Blue Team handles incident response, log analysis, and implementing security measures to prevent breaches.
Skill Sets Required for Red and Blue Teams
Red Team members require advanced penetration testing, social engineering, and exploit development skills to simulate real-world cyberattacks effectively. Blue Team professionals must possess expertise in threat detection, incident response, network defense, and security information and event management (SIEM) tools to protect organizational assets. Both teams benefit from strong knowledge of cybersecurity frameworks, system vulnerabilities, and continuous learning to adapt to evolving threats.
Common Tools and Technologies Used
Red Teams frequently employ tools like Metasploit, Cobalt Strike, and Nmap to simulate attacks and identify network vulnerabilities, while Blue Teams utilize solutions such as Splunk, Wireshark, and Carbon Black for real-time monitoring, threat detection, and incident response. Both teams integrate Security Information and Event Management (SIEM) platforms and Endpoint Detection and Response (EDR) systems to enhance visibility and coordinate defense strategies. Effective collaboration between Red and Blue teams hinges on leveraging these technologies to strengthen overall cybersecurity posture.
Methodologies and Tactics Employed
Red Team employs offensive methodologies such as penetration testing, social engineering, and vulnerability exploitation to simulate realistic cyberattacks and identify security gaps. Blue Team focuses on defensive tactics including continuous monitoring, threat hunting, incident response, and patch management to detect, mitigate, and prevent intrusions. Both teams rely on frameworks like MITRE ATT&CK to align strategies and improve organizational cybersecurity posture.
Collaboration and Communication Strategies
Effective collaboration between Red Teams and Blue Teams hinges on structured communication strategies like joint debriefings, shared documentation, and real-time threat intelligence exchanges. Establishing common frameworks such as MITRE ATT&CK fosters transparent dialogue and aligns offensive tactics with defensive preparedness. Continuous feedback loops enable adaptive learning, enhancing both teams' capabilities to anticipate and mitigate evolving security threats.
Simulating Real-world Attacks: Red Team Perspective
Red Team exercises simulate real-world cyberattacks by emulating tactics, techniques, and procedures (TTPs) used by actual threat actors to identify vulnerabilities in an organization's security posture. This proactive approach enables security teams to assess the effectiveness of existing defenses, uncover blind spots, and improve incident response strategies. Continuous Red Team assessments enhance the resilience of critical assets against evolving cyber threats.
Defensive Response: Blue Team Approach
The Blue Team employs continuous network monitoring and incident response strategies to detect, analyze, and mitigate threats in real-time. Leveraging advanced tools like Security Information and Event Management (SIEM) systems and threat intelligence feeds, they enhance an organization's defense posture and resilience. Regular vulnerability assessments and rigorous patch management ensure minimized attack surfaces and strengthened cybersecurity frameworks.
Red Team vs Blue Team in Security Operations Centers
Red Team simulates advanced cyber-attacks to identify vulnerabilities and test the resilience of Security Operations Centers (SOCs). Blue Team defends SOCs by monitoring, detecting, and responding to threats in real-time to maintain system integrity. Effective collaboration between Red Team and Blue Team enhances threat intelligence, incident response, and overall cybersecurity posture.
Career Paths and Opportunities in Red and Blue Teams
Red Team careers emphasize offensive security skills such as penetration testing, vulnerability assessment, and ethical hacking, offering roles like Red Team Operator, Penetration Tester, and Security Researcher. Blue Team professionals focus on defensive security measures including threat detection, incident response, and security monitoring, with job titles like Security Analyst, Incident Responder, and SOC Engineer. Both career paths provide opportunities for specialization, certification, and advancement within cybersecurity frameworks, driving demand for experts who safeguard organizational assets from evolving cyber threats.
Red Team vs Blue Team Infographic
 jobdiv.com
jobdiv.com