Penetration testers simulate real-world cyberattacks to identify and exploit security weaknesses, providing actionable insights into an organization's defenses. Vulnerability analysts focus on continuously scanning, assessing, and prioritizing system vulnerabilities to support risk management and remediation efforts. Both roles are critical for enhancing an organization's cybersecurity posture but differ in approach and scope.
Table of Comparison
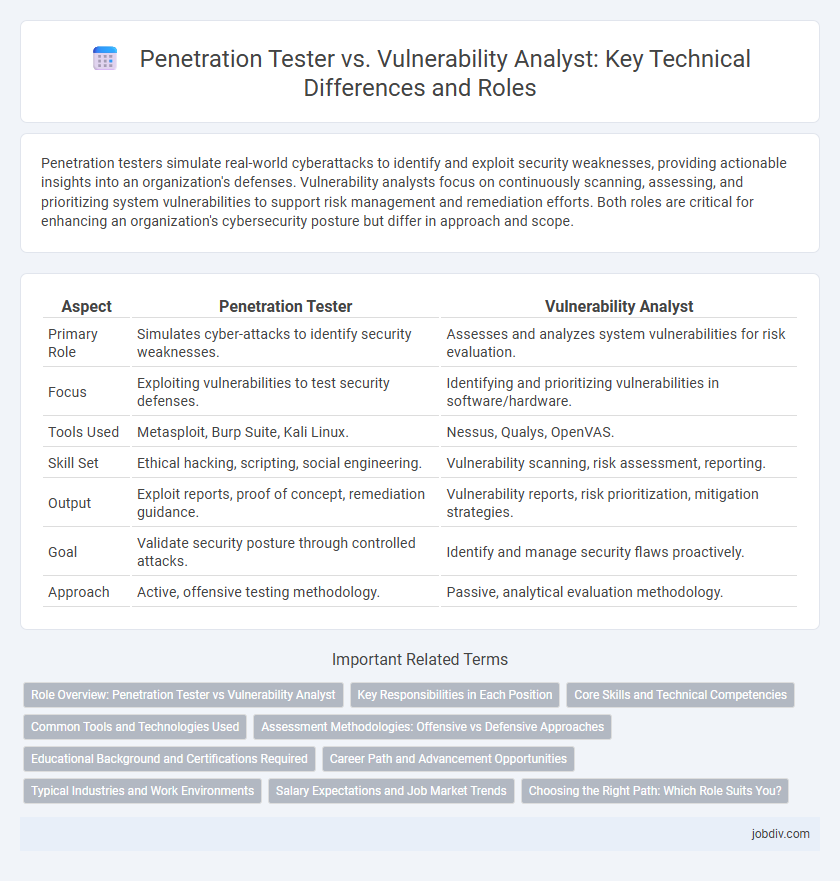
| Aspect | Penetration Tester | Vulnerability Analyst |
|---|---|---|
| Primary Role | Simulates cyber-attacks to identify security weaknesses. | Assesses and analyzes system vulnerabilities for risk evaluation. |
| Focus | Exploiting vulnerabilities to test security defenses. | Identifying and prioritizing vulnerabilities in software/hardware. |
| Tools Used | Metasploit, Burp Suite, Kali Linux. | Nessus, Qualys, OpenVAS. |
| Skill Set | Ethical hacking, scripting, social engineering. | Vulnerability scanning, risk assessment, reporting. |
| Output | Exploit reports, proof of concept, remediation guidance. | Vulnerability reports, risk prioritization, mitigation strategies. |
| Goal | Validate security posture through controlled attacks. | Identify and manage security flaws proactively. |
| Approach | Active, offensive testing methodology. | Passive, analytical evaluation methodology. |
Role Overview: Penetration Tester vs Vulnerability Analyst
Penetration Testers simulate cyberattacks to identify exploitable security weaknesses by actively exploiting vulnerabilities, whereas Vulnerability Analysts systematically assess and prioritize vulnerabilities through automated scanning and manual analysis without direct exploitation. Penetration Testers provide real-world attack insights to test defenses, while Vulnerability Analysts focus on continuous monitoring and risk assessment to support remediation efforts. Both roles are critical for comprehensive cybersecurity, combining proactive exploitation with detailed vulnerability management.
Key Responsibilities in Each Position
Penetration Testers simulate cyberattacks to identify and exploit security weaknesses in networks, applications, and systems, focusing on real-world attack scenarios and vulnerability exploitation. Vulnerability Analysts assess and prioritize security vulnerabilities by scanning systems, analyzing threat data, and recommending remediation strategies to enhance an organization's security posture. Both roles require expertise in cybersecurity tools and techniques, but penetration testers emphasize offensive tactics while vulnerability analysts concentrate on defensive analysis and risk management.
Core Skills and Technical Competencies
Penetration testers excel in ethical hacking techniques, exploit development, and adversarial simulation to identify security weaknesses by simulating real-world attacks. Vulnerability analysts specialize in vulnerability assessment, risk analysis, and patch management using tools like Nessus, Qualys, and OpenVAS to prioritize threats and recommend remediation strategies. Both roles require proficiency in network protocols, operating systems, scripting languages, and security frameworks such as OWASP and NIST.
Common Tools and Technologies Used
Penetration testers commonly utilize tools like Metasploit, Burp Suite, and Nmap for exploiting vulnerabilities and simulating real-world attacks. Vulnerability analysts often rely on automated scanners such as Nessus, Qualys, and OpenVAS to identify and assess security weaknesses systematically. Both roles leverage technologies like Kali Linux and Wireshark to support comprehensive security evaluations and network analysis.
Assessment Methodologies: Offensive vs Defensive Approaches
Penetration testers employ offensive assessment methodologies that simulate real-world cyberattacks to identify exploitable vulnerabilities by actively attempting to breach systems. Vulnerability analysts utilize defensive approaches by systematically scanning, analyzing, and prioritizing security weaknesses to recommend patching and remediation strategies. The contrast lies in penetration testing's exploit-driven tactics versus vulnerability analysis's risk assessment and mitigation focus.
Educational Background and Certifications Required
Penetration testers typically require a strong foundation in computer science or cybersecurity, often holding degrees in information technology, computer engineering, or related fields, along with certifications such as OSCP (Offensive Security Certified Professional) or CEH (Certified Ethical Hacker). Vulnerability analysts benefit from education in cybersecurity, information assurance, or network security, paired with certifications like CISSP (Certified Information Systems Security Professional) or CompTIA Security+ that emphasize risk assessment and vulnerability management. Both roles demand ongoing professional development to stay current with evolving security threats and technologies.
Career Path and Advancement Opportunities
Penetration Testers typically advance by developing expertise in ethical hacking, obtaining certifications such as OSCP or CEH, and moving into roles like Senior Pen Tester, Security Consultant, or Red Team Lead. Vulnerability Analysts progress by deepening their skills in vulnerability assessment tools, risk management, and compliance frameworks, often advancing to positions like Vulnerability Manager, Security Analyst, or Information Security Officer. Career growth for both paths benefits from continuous learning in cybersecurity trends and mastery of industry standards such as NIST, ISO 27001, and CVSS scoring systems.
Typical Industries and Work Environments
Penetration testers primarily operate within cybersecurity firms, financial institutions, and government agencies, where proactive security assessments simulate real-world attacks to identify system weaknesses. Vulnerability analysts are commonly employed across healthcare, manufacturing, and technology sectors, focusing on continuous vulnerability scanning and risk management to maintain compliance and secure infrastructure. Both roles typically work in dynamic, high-security environments requiring collaboration with IT and security teams to strengthen organizational defenses.
Salary Expectations and Job Market Trends
Penetration Testers generally command higher salary expectations due to their specialized skills in simulating cyber attacks and identifying security weaknesses. Vulnerability Analysts focus on continuous monitoring and risk assessment, resulting in competitive but often slightly lower compensation compared to Penetration Testers. The job market trends indicate a growing demand for both roles, with Penetration Testers experiencing faster salary growth driven by an increased emphasis on proactive security measures in enterprise IT environments.
Choosing the Right Path: Which Role Suits You?
Penetration Testers simulate cyberattacks to identify exploitable security weaknesses, requiring strong offensive skills and creativity in breach techniques. Vulnerability Analysts focus on systematically scanning, assessing, and prioritizing vulnerabilities to recommend remediation, emphasizing analytical rigor and risk management. Choosing the right path depends on your preference for proactive exploitation versus in-depth vulnerability assessment within cybersecurity frameworks.
Penetration Tester vs Vulnerability Analyst Infographic
 jobdiv.com
jobdiv.com