Penetration testers actively simulate cyberattacks to identify exploitable security weaknesses, while vulnerability assessors systematically scan and report potential vulnerabilities without direct exploitation. Penetration testing provides deeper insights by demonstrating real-world impacts, whereas vulnerability assessments offer broad visibility into system risks. Organizations benefit from combining both approaches to strengthen their security posture and prioritize remediation efforts effectively.
Table of Comparison
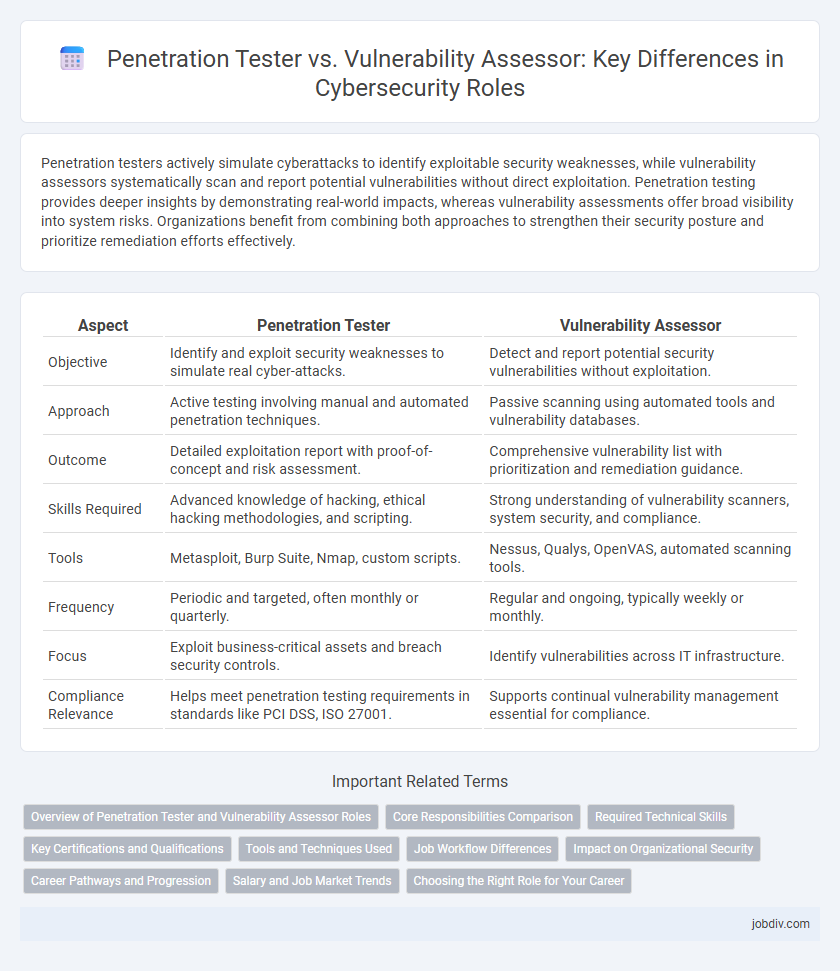
| Aspect | Penetration Tester | Vulnerability Assessor |
|---|---|---|
| Objective | Identify and exploit security weaknesses to simulate real cyber-attacks. | Detect and report potential security vulnerabilities without exploitation. |
| Approach | Active testing involving manual and automated penetration techniques. | Passive scanning using automated tools and vulnerability databases. |
| Outcome | Detailed exploitation report with proof-of-concept and risk assessment. | Comprehensive vulnerability list with prioritization and remediation guidance. |
| Skills Required | Advanced knowledge of hacking, ethical hacking methodologies, and scripting. | Strong understanding of vulnerability scanners, system security, and compliance. |
| Tools | Metasploit, Burp Suite, Nmap, custom scripts. | Nessus, Qualys, OpenVAS, automated scanning tools. |
| Frequency | Periodic and targeted, often monthly or quarterly. | Regular and ongoing, typically weekly or monthly. |
| Focus | Exploit business-critical assets and breach security controls. | Identify vulnerabilities across IT infrastructure. |
| Compliance Relevance | Helps meet penetration testing requirements in standards like PCI DSS, ISO 27001. | Supports continual vulnerability management essential for compliance. |
Overview of Penetration Tester and Vulnerability Assessor Roles
Penetration testers simulate cyberattacks to identify and exploit security weaknesses within systems, networks, or applications, providing a practical demonstration of vulnerabilities. Vulnerability assessors systematically scan and analyze IT environments to detect and categorize potential security flaws without actively exploiting them. Both roles are critical in cybersecurity, with penetration testers offering hands-on threat simulation and vulnerability assessors delivering comprehensive risk assessments.
Core Responsibilities Comparison
Penetration testers simulate real-world cyberattacks to identify exploitable security weaknesses by actively attempting to breach systems, while vulnerability assessors perform comprehensive scans and analyses to identify and report potential vulnerabilities without exploiting them. Penetration testers deliver detailed reports on attack paths and risk impact, emphasizing exploit validation, whereas vulnerability assessors provide prioritized lists of vulnerabilities with remediation advice. Both roles are essential in cybersecurity, with penetration testing focusing on practical breach scenarios and vulnerability assessment emphasizing broad security posture evaluation.
Required Technical Skills
Penetration testers require advanced skills in ethical hacking, exploit development, and network protocol analysis to simulate real-world cyberattacks effectively. Vulnerability assessors focus on expertise in automated scanning tools, vulnerability databases, and remediation reporting to identify and prioritize security weaknesses. Both roles demand proficiency in operating systems, scripting languages, and security frameworks, but penetration testers emphasize offensive strategies while vulnerability assessors concentrate on defensive risk assessment.
Key Certifications and Qualifications
Penetration testers often hold certifications such as Offensive Security Certified Professional (OSCP), Certified Ethical Hacker (CEH), and GIAC Penetration Tester (GPEN), emphasizing hands-on exploit skills and real-world attack simulations. Vulnerability assessors typically pursue certifications like Certified Vulnerability Assessor (CVA), CompTIA Security+, and Certified Information Systems Security Professional (CISSP), highlighting risk analysis, vulnerability identification, and remediation strategies. Both roles benefit from strong knowledge of network protocols, security frameworks, and tools such as Nessus, Metasploit, and Burp Suite to enhance cybersecurity defenses.
Tools and Techniques Used
Penetration testers employ advanced tools like Metasploit, Burp Suite, and Kali Linux to simulate cyberattacks, focusing on exploiting system vulnerabilities and assessing real-world security risks. Vulnerability assessors primarily use automated scanners such as Nessus, Qualys, and OpenVAS to identify and classify security weaknesses without actively exploiting them. Both roles leverage scripting languages like Python and employ techniques including network scanning, vulnerability scanning, and manual testing to enhance organizational cybersecurity posture.
Job Workflow Differences
Penetration testers simulate real-world cyberattacks to identify and exploit security weaknesses, providing actionable insights through hands-on testing and reporting on system vulnerabilities. Vulnerability assessors systematically scan and analyze systems to detect potential security flaws, focusing on comprehensive vulnerability identification without exploiting them. The job workflow of penetration testers involves active exploitation and scenario-based testing, whereas vulnerability assessors emphasize automated tools and detailed vulnerability reporting for remediation.
Impact on Organizational Security
Penetration testers simulate real-world cyberattacks to identify exploitable vulnerabilities, providing organizations with insights into potential breach scenarios and the effectiveness of their security defenses. Vulnerability assessors conduct comprehensive scans to detect and classify security weaknesses, enabling organizations to prioritize remediation efforts and reduce overall risk exposure. The combined use of both roles strengthens organizational security by addressing both the technical vulnerabilities and the practical implications of attacks.
Career Pathways and Progression
Penetration testers specialize in exploiting system vulnerabilities through simulated attacks, developing advanced skills in ethical hacking and exploit development, making them ideal for roles in cybersecurity defense and threat analysis. Vulnerability assessors focus on identifying and evaluating security weaknesses using automated tools and manual techniques, often progressing towards roles in risk management and compliance auditing. Career pathways for penetration testers often lead to positions like security consultant or red team lead, while vulnerability assessors may advance to security analyst or governance, risk, and compliance (GRC) specialist roles.
Salary and Job Market Trends
Penetration testers typically command higher salaries, averaging between $90,000 and $130,000 annually due to specialized skills in ethical hacking and exploit identification. Vulnerability assessors earn slightly less, with average salaries ranging from $70,000 to $110,000, reflecting their focus on identifying security weaknesses without exploitation. The job market for penetration testers is growing rapidly, driven by increased cybersecurity threats and compliance requirements, while demand for vulnerability assessors remains steady as organizations prioritize continuous security monitoring.
Choosing the Right Role for Your Career
Selecting between a penetration tester and a vulnerability assessor depends on your career goals in cybersecurity. Penetration testers simulate real-world cyber attacks to identify system weaknesses, requiring advanced skills in ethical hacking and exploit development. Vulnerability assessors focus on scanning and analyzing systems for security flaws, emphasizing detailed reporting and risk management, making it ideal for professionals interested in continuous monitoring and compliance.
Penetration Tester vs Vulnerability Assessor Infographic
 jobdiv.com
jobdiv.com